Once the attacker has gained initial access to the network, they deploy further tools to control the devices they have compromised and use those tools to carry out the next steps of the attack.
How the attacker attempts to gain access to all devices
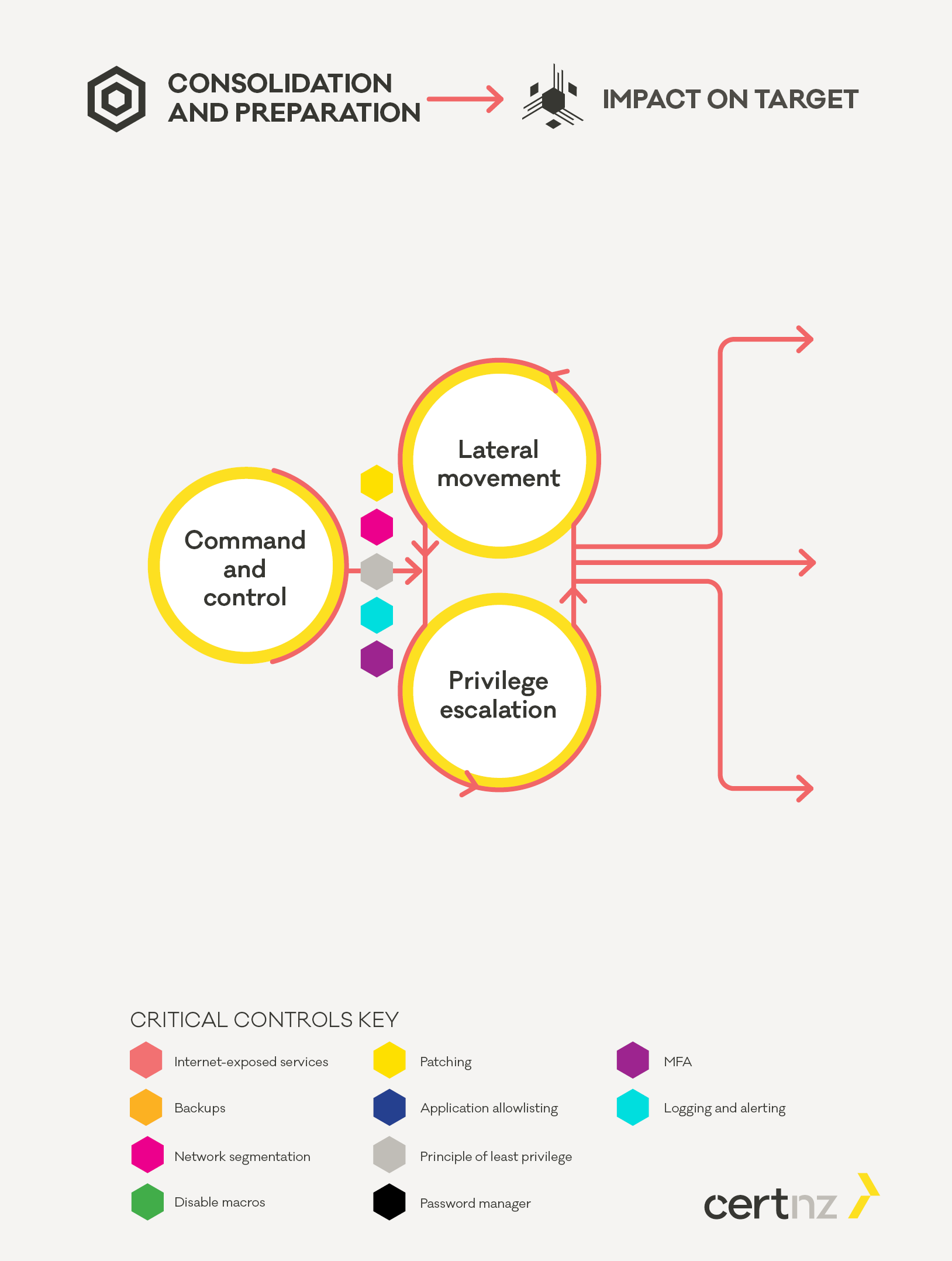
The attackers goal is to gain access to all relevant devices in the environment including servers and workstations. To achieve this, the attackers will look for a path to gain Domain Administrator privileges as well as access to key infrastructure such as:
- backup servers
- control panels for security systems such as Security Information and Event Management (SIEM) or Endpoint Detection and Response (EDR)
- virtualisation platforms such as VMWare VCenter.
Command and control (C2)
An important part of moving from a single compromised device to the entire network is establishing command and control to deploy and run additional tooling. C2 tools such as Cobalt Strike are used to deploy and run other tools such as Bloodhound and mimikatz, which are used in the next step. Other capabilities of the C2 tool may be used to carry out discovery of other devices on the network, establish persistence on devices and obfuscate these activities.
ATT&CK® Techniques
- T1573 Encrypted Channel External Link
- T1078 Account Discovery External Link
- T1018 Remote System Discovery External Link
- T1046 Network Service Scanning External Link
Commonly used tools
Application allowlisting supported by logging and alerting form key defences to stop an attacker. Modern security tools are kept up to date by their developers to be able to detect tools like Cobalt Strike. Preventing these from running or responding rapidly if they are detected in your environment is key to preventing further compromise.
Lateral movement and Privilege escalation
These steps happen in tandem, with the attacker using C2 capabilities to deploy additional tools and identifying pathways to higher privileges. Once identified the attacker attempts to follow those paths combining steps of compromising credentials and using those credentials to access other devices on the network.
Privilege escalation is often a combination of compromising credentials using tools such as mimikatz and exploiting vulnerabilities in operating systems and applications to gain administrative access to systems.
Lateral movement is often carried out using tools native to the operating system of the devices such as PowerShell, RDP, and SMB. By using native tools the attacker reduces the likelihood of a defender noticing new tools that have been deployed in the network.
In this phase attackers will often identify security products in use and attempt to either obfuscate their activities or disable security controls such as endpoint protection in order to avoid detection. This activity often takes place outside an organisations regular working hours in order to reduce the likelihood of timely detection and response.
ATT&CK® refs
- T1582 Domain Trust Discovery External Link
- T1069 Permission Groups Discovery External Link
- T1003 OS Credential dumping External Link
- T1068 Exploitation for Privilege Escalation External Link
- T1078 Valid Accounts External Link
- T1021 Remote Services External Link
- T1570 Lateral Tool Transfer External Link
Commonly used tools
- S0002 mimikatz External Link
- S0521 Bloodhound External Link
- OS native tools such as psexec, RDP, SMB, WMIC
As defenders we have two goals: limit the ability of the attacker to access other systems and prevent the attacker from gaining higher privilege credentials. In many cases controls support both of these objectives simultaneously.
For example: by having administrators use separate accounts on separate computers that are segmented off from the rest of the workstations in your environment, you make it more difficult to gain access to those credentials and computers. This combines the principle of least privilege and network segmentation.
Aside from separating administrative devices from the rest of the environment network segmentation is a fundamental control to limit the scope of an attacker. If the attacker cannot communicate with their intended targets, then their options will be greatly limited. Firewalls can also provide an excellent source of information to support your logging and alerting of unusual or suspicious activity.
Endpoint security tools that limit what applications can be run - along with logging and alerting - can alert you to activity such as Bloodhound or other tools the attackers may attempt to deploy or use.
Applying the principle of least privilege helps prevent an attacker from using compromised credentials to gain administrative access or access to other systems. It also means that an attacker should not immediately gain access to all data on shared network drives, for example. Nor should they be able to turn off defensive controls such as Shadow Copy on Windows devices or disable endpoint protection software.
If an attacker does gain credentials that can be used to access other systems, enforcing multi-factor authentication can help limit their ability to spread across the environment. This is especially important and valuable for administrative consoles which are less commonly accessed but are a particularly useful target for an attacker.
Patching all devices in your environment in a timely manner is important to prevent those vulnerabilities being used to gain further access.
Supporting all defensive activities is a strong logging and alerting capability with alerts being followed up and investigated. An example of an event which should be considered high priority for investigation is any device where endpoint protection tools are suddenly disabled. This can indicate an attacker that is attempting to hide their activity, or carrying out activity that your security tools would have blocked.
If you detect an attacker active on your network it is important to make sure you have identified the full extent of their access before you carry out activity to evict them from your environment. Attackers have been seen to rapidly move to impact on target when they realise that eviction is imminent.
The defences you apply here are vital to limiting the spread of an attacker that has gained access to your network. By ensuring an attacker cannot gain access to other systems and preventing them from gaining administrative access, you limit the damage they can do. This is useful for mitigating any network compromise regardless of the attackers end goal or how they gained initial access. However, if an attacker is able to achieve their goals in this phase, then they will move to the impact on target phase, where destructive activity is carried out.
