Summary
Credential harvesting and unauthorised access causes a large number of incidents reported to CERT NZ, and can lead to larger issues when users have excessive or administrative permissions. Getting access to an account with a lot of permissions is great for attackers as they have more access to data and systems. This makes it easier to get more information and easier to go undetected.
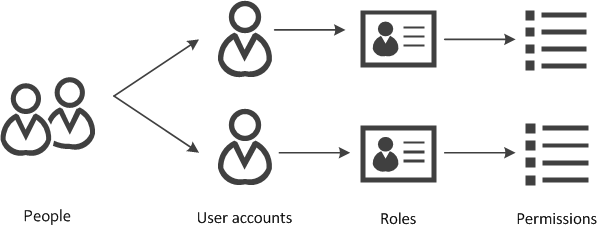
These attacks can be mitigated by implementing role-based access control. Permissions can be assigned to a role. User accounts can have more than one role assigned. People can have more than one user account. For example if someone needs administrative access we recommend giving them an administrative user account for those particular tasks and a second user account with lesser privileges for everyday use. Different systems allow differing levels of controls or may use different terms, check your system documentation for how your system works.
You can also consider implementing just-in-time (JIT) access to mitigate the risk of privileged account access. Using JIT access can help organisations provision access so that users only have access to privileged accounts and resources for a specific timeframe.
Purpose
The intent of this control is for organisations to know what access user accounts have to each system and ensure they only have the access they need to do their jobs.
Measuring success
Implementing this control requires you to look at your:
- systems
- access methods, and
- permissions.
The goals for your organisation are to have an understanding of access in your environment and to have operational processes in place as detailed below.
High level understanding
Your organisation understands:
- the minimum level of permissions needed for all jobs within your organisation, and
- the permissions that are assigned to roles within each system. This will allow you to know if a user with that role has the right permissions for their job.
You or your team has a complete view of:
- the permissions and roles that every user has for each system
- the systems in your environment and how users access them, either through a front end application or through the back end infrastructure. This includes user accounts that your staff use, and system and service accounts that are not regularly accessed by staff.
Operational processes
Your organisation has a method or a process to:
- identify the permissions a user needs before you give or change any access
- review users to make sure they keep the smallest level of permissions needed for their job
- identify when a change has happened that may need changes to the permissions, roles, or users in a system
- remove users that are no longer needed
- assign separate accounts to users who need administrative or sensitive permissions. One account has the administrative permissions, and the other has lesser permissions for other aspects of their job.
- log actions taken by administrative users and send the logs to a central location. Configure them to send an alert to feed into your incident or change management processes.
Least privilege: Key takeaways
- If you’re unsure which permissions a user account needs, give less access. If they can’t do an aspect of their job, they can ask for extra permissions. Update any documents you have to keep track of what permissions a job needs and why.
- Sometimes it’s challenging to understand what level of access a system account needs. When in doubt, assign a lower level of access and test it. If the service or system account requires administrative permissions, make sure you understand what those permissions are used for.
- Avoid copying access from one user account to another without reviewing it. The copied account might have additional permissions that aren’t necessary for the new person.
- Be critical of giving out administrative access. It’s OK to ask these users why they may need those permissions and what tasks they need to perform. Instead of giving your CIO administrator access to keep an eye on things, configure alerts and reports so they can monitor use of administrative actions.
- Log and analyse all administrative actions to identify any suspicious or abnormal behaviour.
- Take an additional step to protect your user accounts and make sure all internet-facing and administrative services are also protected with multi-factor authentication.
Advice for implementation
Enforcing the principle of least privilege