Once the attacker has access to all relevant parts of the environment they will seek to extract sensitive information, destroy your organisations backups and finally encrypt your systems and data.
How the attacker steals and encrypts data, then demands ransom
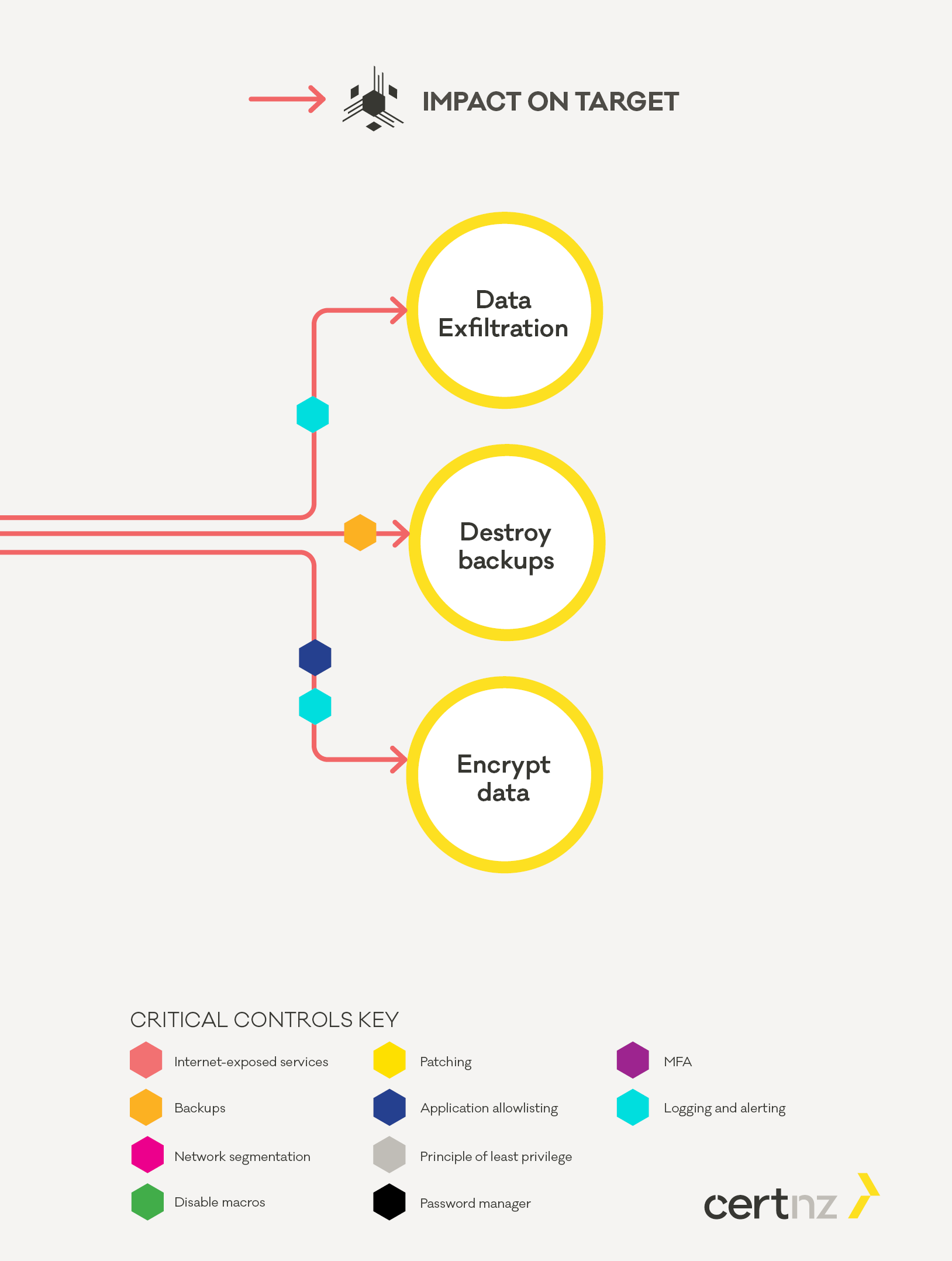
In most cases data will be staged and exfiltrated slowly to avoid setting off Data Loss Prevention (DLP) or similar. Increased and recurring data uploads to unknown web services or common external file and data storage services such as Mega or Dropbox are common signs of data exfiltration. Exhaustive access to internal files and data stores by user accounts are also common signs.
Look for users who are suddenly accessing data not associated with their role in bulk or privileged accounts accessing data rather than standard user accounts. As with the previous phase much of this activity has been seen to occur overnight or otherwise outside normal business hours in order to reduce the likelihood of detection and response.
Once all desired data has been exfiltrated the attackers will seek to destroy your backups and then encrypt your data. At this point ransom notes or lock screens will be deployed to alert you to the ransomware attack and usually provide instructions about payment. These will often include instructions for payment to decrypt your data as well as a second payment to prevent the attacker from leaking or selling the data they have taken from your environment. They may also threaten further activity such as Distributed-Denial-of-Service (DDoS).
ATT&CK® Techniques
- T1005 Data from Local System External Link
- T1039 Data from Network Shared Drive External Link
- T1560 Archive Collected Data External Link
- T1567 Exfiltration over Web Service External Link
- T1537 Transfer Data to Cloud Account External Link
- T1490 Inhibit System Recovery External Link
- T1486 Encrypt Data for Impact External Link
In this phase the attacker has already achieved the access they want and the window for detection and disruption is small. With careful analysis you may be able to detect data being exfiltrated from your network. Unfortunately this is often only detected after the fact by forensic investigators.
Some endpoint protection tools have had some success in detecting the malware that is carrying out the encryption and stopping the process however this is not guaranteed. Without immediate follow-up with further incident response activity it is possible an attacker will still succeed.
The most important control when an attacker has reached this phase of the attack is having a robust and well tested backup system. As attackers are known to destroy backups, techniques such as offline or disconnected backups are critical in order to recover from the encryption.
When working on your incident response plan consider how your team will work when your organisations normal business systems, such as email, are down. It’s possible your incident response plan itself will be encrypted so it’s important to have hard copies and other offline copies available. Documents including key contacts, BCP and DR plans should also be considered.
During a complex incident response communication is key so establishing how you and your stakeholders are going to communicate ahead of time can pay dividends during an incident.
If your organisation is hit with a ransomware attack report it to CERT NZ and break out your incident response plan.
