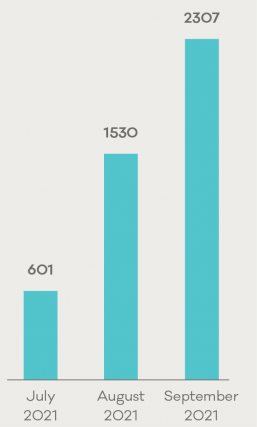
This quarter, CERT NZ responded to 2,072 incident reports about individuals and businesses from all over New Zealand. This report shares information around these incidents as well as highlighting examples of work CERT NZ is doing to help. There are two parts to the report:
A Highlights Report focusing on selected cyber security incidents and issues.
A Data Landscape Report providing a standardised set of results and graphs for the quarter.
Highlights
2,072 incidents were responded to by CERT NZ in Q3 2021
$3.3 million in direct financial loss was reported in Q3. 16% of incidents reported financial loss
Malware reports increased from 32 in Q2 to 151 in Q3
Scams and fraud reports increased by 25%
The average number of incident reports per quarter is 1,623 and average direct financial loss per quarter is $4.1 million. These figures are based on the previous eight quarters.
Incident numbers
A total of 2,072 incidents were responded to in Q3 2021.
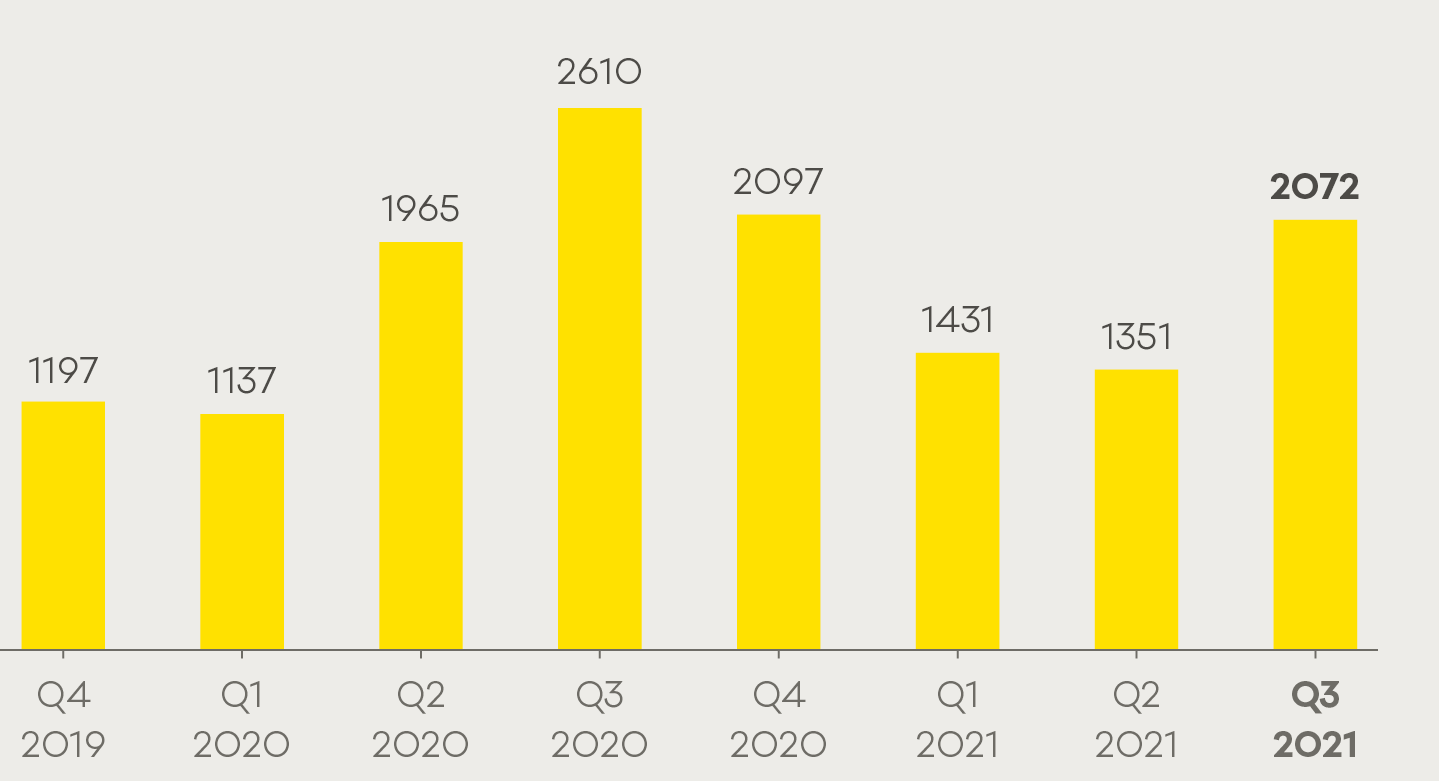
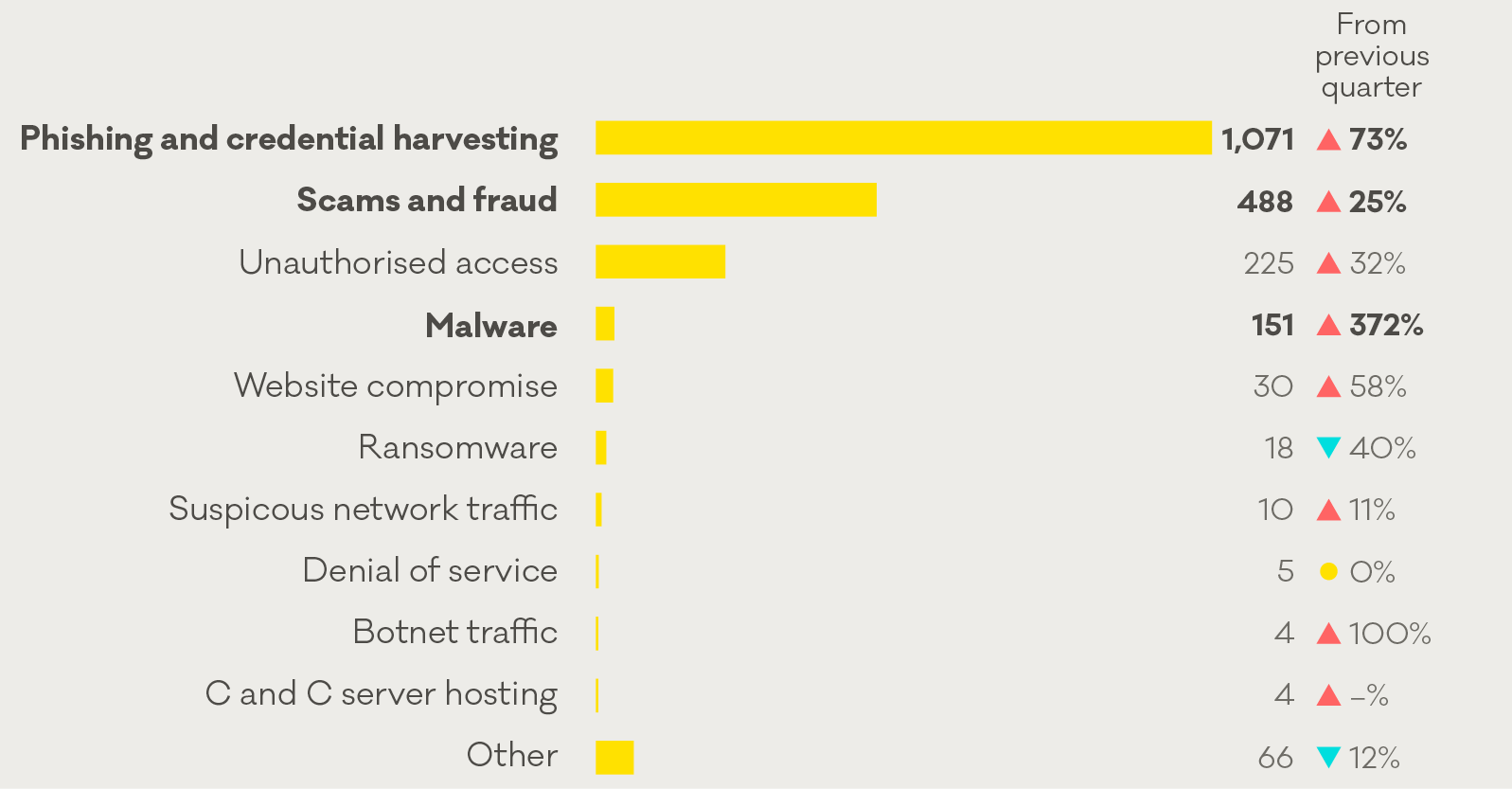
Breakdown of incident category
Phishing and credential harvesting remains the most reported incident category, with 1,071 reports in Q3. A 73% increase on the previous quarter.
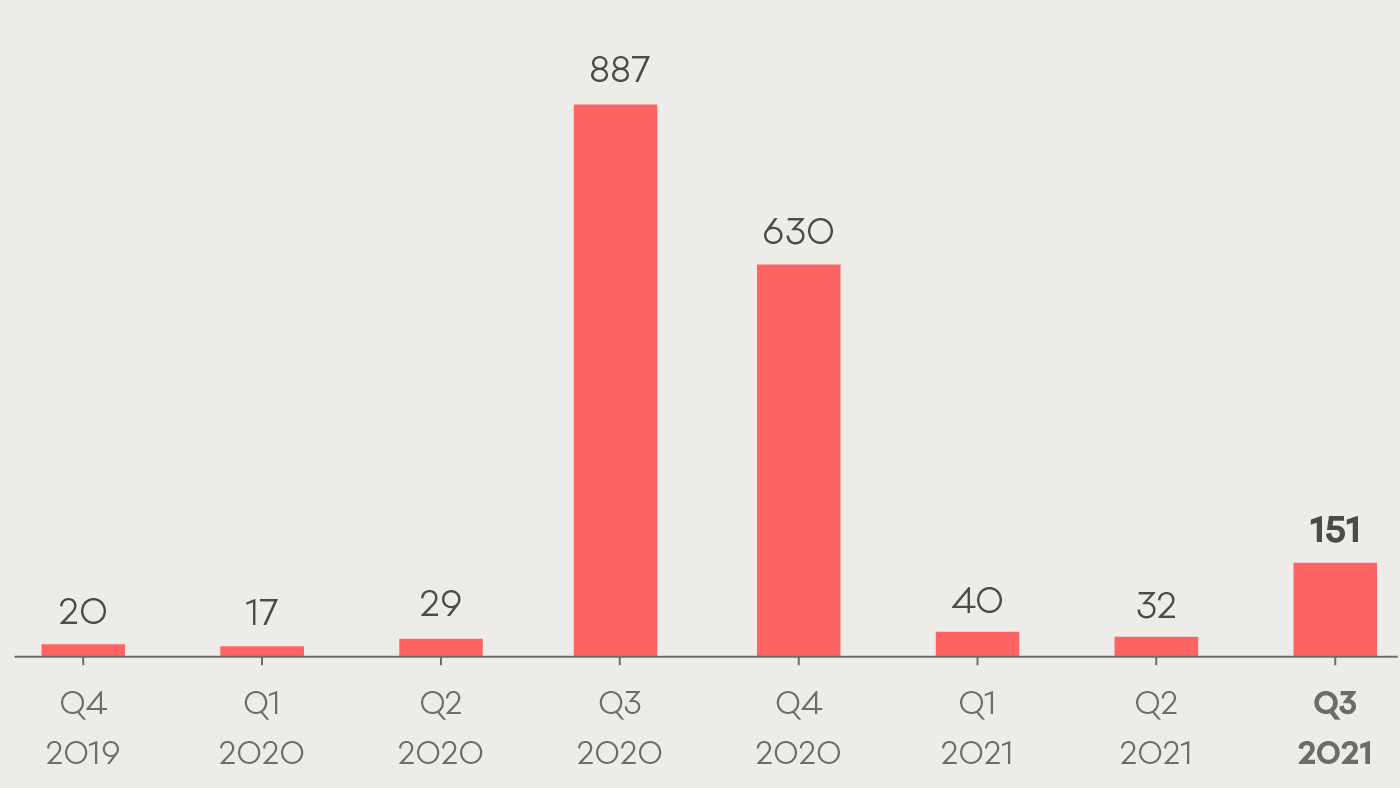
Focus area: Malware incidents more than triple
In Q3, malware reports more than tripled from the previous quarter (from 32 to 151 reports). Malware is malicious software designed to go unnoticed and damage or compromise a computer system.
Number of malware reports to CERT NZ
Protecting from malware
As with most cyber security threats, having protections in place to reduce the risk of an attack is much easier than recovery. CERT NZ recommends that you:
- update operating system and apps when new versions are available and turn on automatic updates where possible.
- enable two-factor authentication on your important accounts like banking or your business’s website to add another layer of security.
Worm-like malware affecting Android phones
In the last week of Q3, we saw the global malware variant FluBot begin large-scale targeting of New Zealand mobile phones. These incidents contributed to this quarter’s spike in malware reports.
How FluBot works
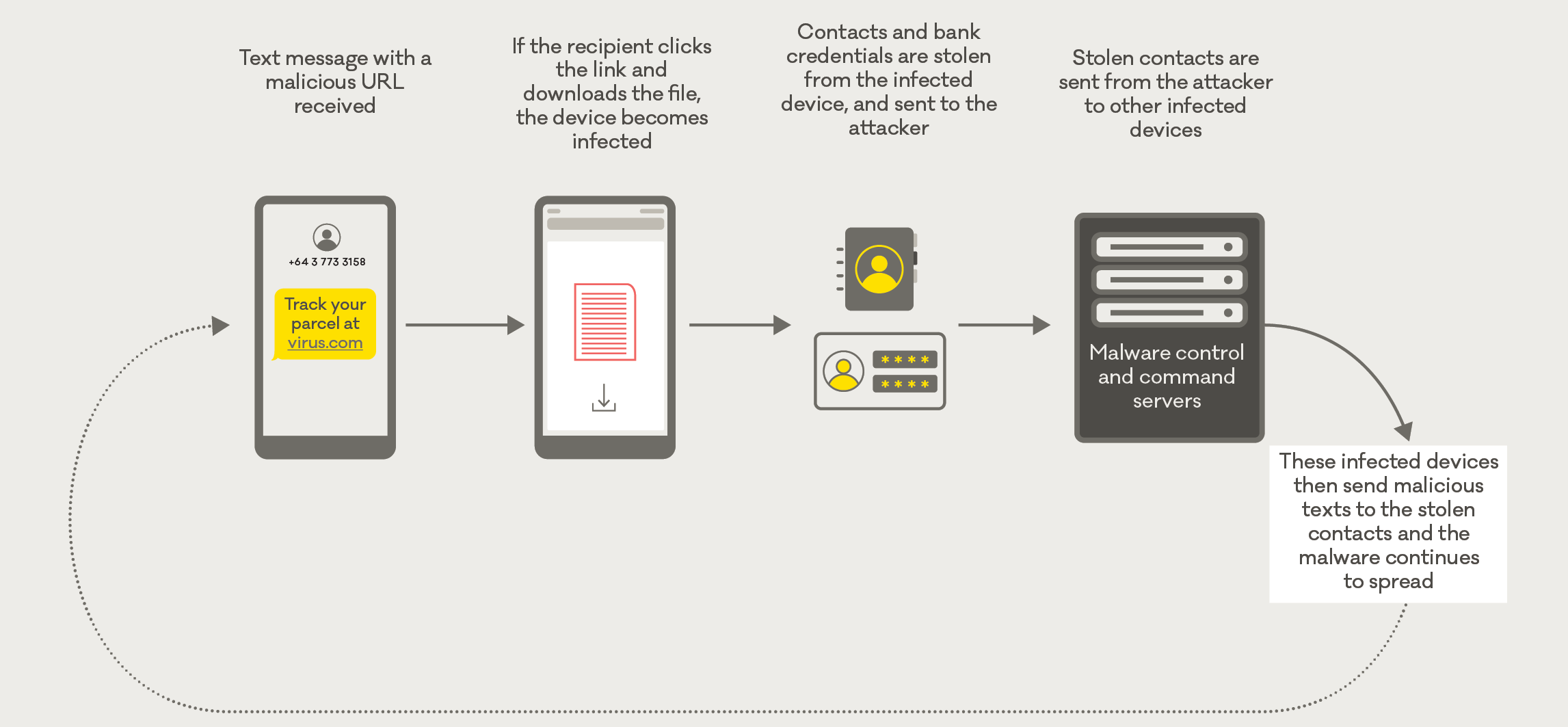
Responding to FluBot
What did CERT NZ do?
CERT NZ partnered with the Digital Safety team at The Department of Internal Affairs (DIA) to lead the government response to the incident.
If you have clicked a link and downloaded FluBot
CERT NZ recommends doing a factory reset on your device as soon as possible. This will delete any data on your phone, including personal data.
Protecting from FluBot
- If you receive a suspicious text message, do not click on the link and do not follow any prompts to install an app or security update. Report the text by sending it, free-of-charge, to DIA on 7726.
- If you are expecting a delivery, don’t click on any links—it’s best to track the delivery by going directly to the courier’s website.
Insight: Online services disrupted by denial-of-service attacks
A denial-of-service (DoS) attack is when an attacker sends malicious internet traffic with the aim of restricting or disrupting user access to a computer system or network. These attacks typically target servers to make websites and payment services unavailable — preventing legitimate users from accessing them.
How CERT NZ helps
Where possible, CERT NZ works with the affected organisation to provide guidance and support to mitigate an attack. The first step when responding to a DoS report is to determine how the organisation’s systems are being impacted. This helps our Incident Response team to understand the internet traffic the affected organisation is seeing and the impacts that traffic is having on their services.
How organisations can protect from DoS attacks
As there isn’t a one-step approach to protecting from a DoS attack, CERT NZ recommends making sure your organisation has defences and mitigations in place, and an incident response plan prepared.
On our website, we have covered the steps to best protect and mitigate a DoS attack. Check with your IT team or service provider that you have these in place.
Preparing for denial of service incidents
If you think you’ve been affected by a DoS attack, please report it to CERT NZ.
Insight: How IoT devices can be used in DDoS attacks
This quarter we continued to see networks of IoT (Internet of Things) devices being used in DDoS attacks. This happens when insecure internet-connected devices, like routers and WiFi-connected cameras, become infected with malware.
How IoT devices can be used in DDoS attacks
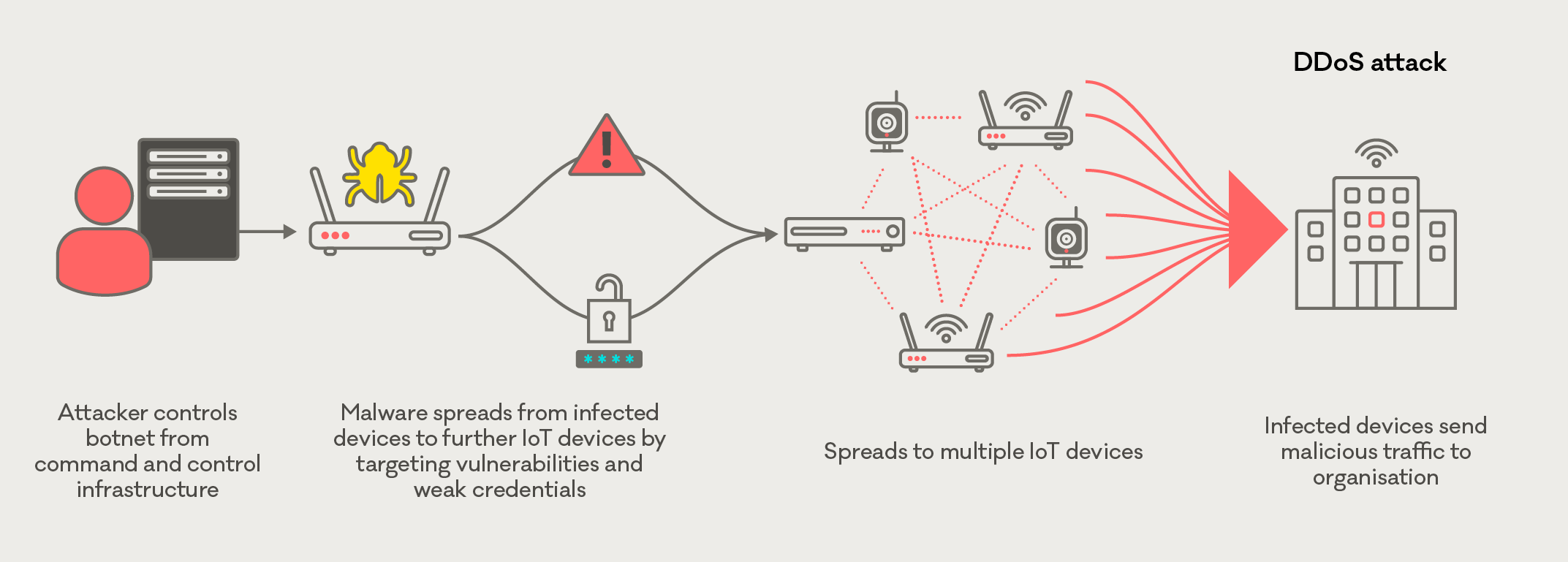
Prevent your devices from being part of an IoT botnet
There are some simple steps you can take to prevent your IoT devices from being used for malicious activity like a DDoS attack.
- Install updates as soon as they are available.
- Make sure you change default passwords or weak passwords wherever possible.
CERT NZ recommends considering whether you need the device connected to the internet. If not, disconnect it.
Botnets can also target non-IoT devices like computer networks. To protect computer networks from becoming part of a botnet please follow malware protection tips
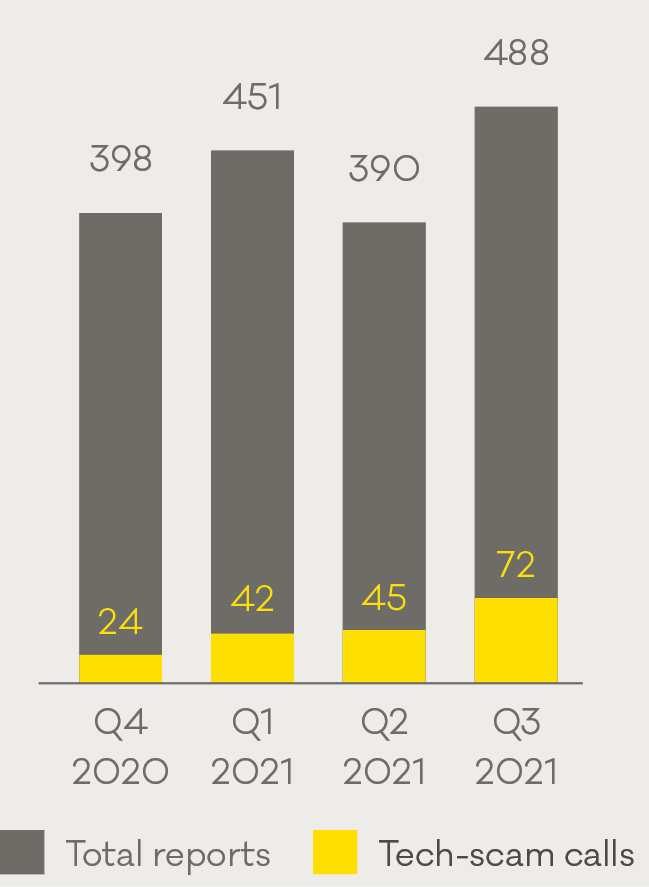
Case study: CERT NZ helps recover funds following tech-scam call
Scams and fraud is consistently one of the highest-reported incident categories to CERT NZ. In Q3, there were 488 scam reports, and 15% were about tech-scam calls.
Scam and fraud reports in Q3 2021
Protecting from a tech-scam call
- If you receive a call about a technical issue with your PC or device, do not provide any information over the phone or allow the caller to have remote access.
- If you are concerned that there is an issue with your PC or device, contact the store you purchased it from or seek help from a trusted IT professional.
If you think you’ve been affected by a scam, please report to CERT NZ