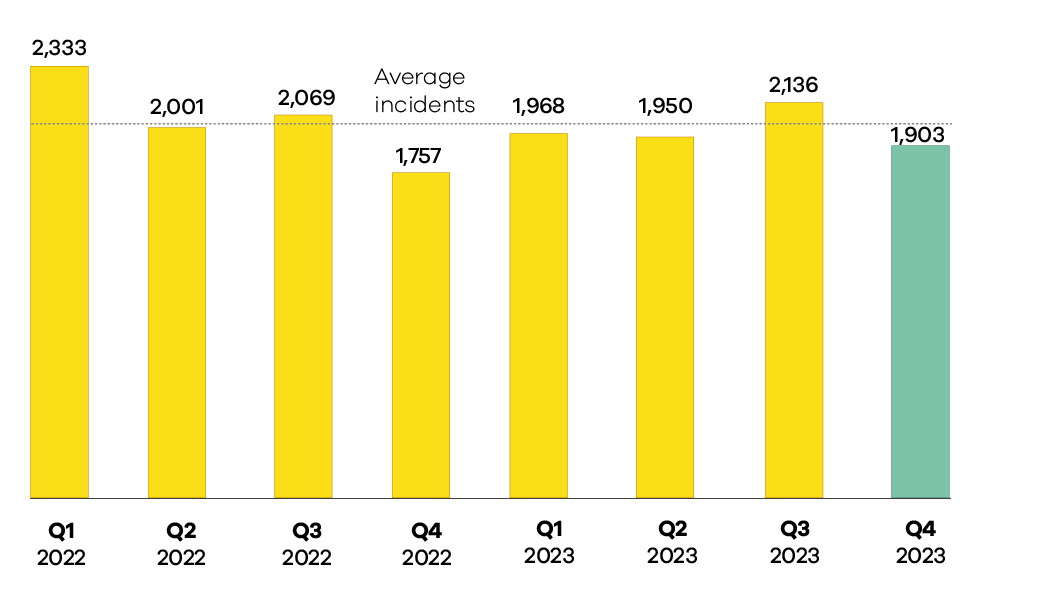
This quarter, CERT NZ responded to 1,903 incident reports about individuals and businesses from all over Aotearoa. This report shares information about these incidents as well as highlights examples of work CERT NZ is doing to help. There are two parts to the report:
A Highlights Report focusing on selected cyber security incidents and issues.
A Data Landscape Report providing a standardised set of results and graphs for the quarter.
- Quarterly Report: Highlights Q4 2023 [PDF, 2.1 MB]
- Quarterly Report: Data Landscape Q4 2023 [PDF, 1.5 MB]
Please note the Data Highlights Report and the Data Landscape Report were updated in May 2024 with minor adjustments to the number of reported incidents.
Highlights
$3.6 million in direct financial loss was reported in Q4, down 24% from Q3 2023. 19% of incidents reported financial loss.
1,903 incidents were responded to by CERT NZ in Q4 2023, down 11% from Q3 2023.
There was a decrease in reports across nearly all incident categories. Scams and fraud reports decreased 22% from Q3 2023.
Scam calls – a subset of scams and fraud – saw a significant increase due to a campaign targeting immigrants.
Number of incidents responded to
A total of 1,903 incidents were responded to in Q4 2023.
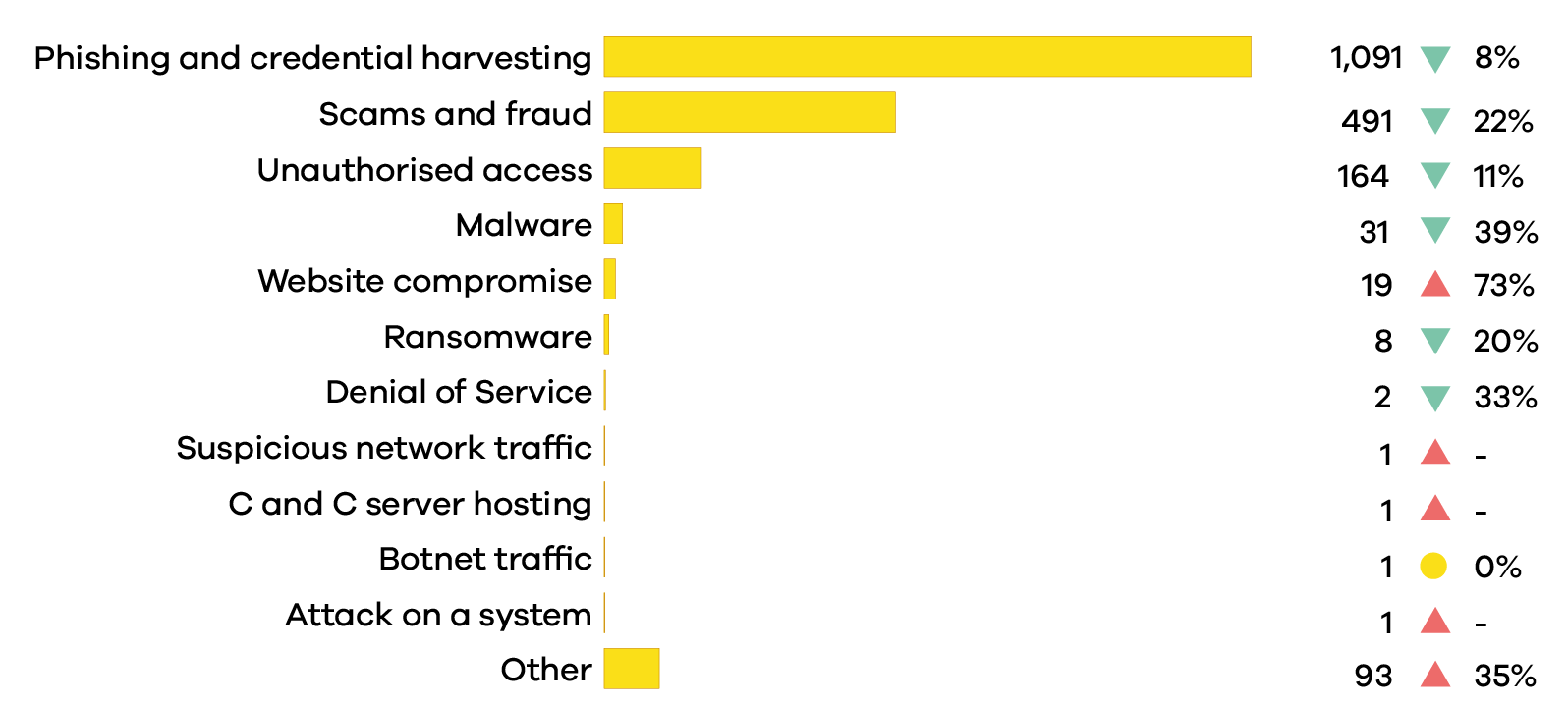
Breakdown by incident category
Phishing and credential harvesting remains the most reported incident category in Q4 2023.
Focus Area: Part and Parcel
It’s a scam most of us are familiar with. You get a text saying there's a problem with your parcel, it can’t be delivered, delivery fees are pending, or your information is not up to date. Then it tells you to click on a link.
Many of us have learnt to identify this as phishing and ignore it. But it’s hard to be a sceptic all the time. What if you have purchased something online and are expecting a parcel? Or what if it's the festive season and someone could be sending you a gift? You click on the link and the landing page asks you for details: name, address, sometimes even credit card information. You enter all that only to realise there is no parcel. There never was.
While reports of such parcel-delivery scams are common throughout the year, CERT NZ noticed that the number increased significantly in the last quarter of 2023 as the holiday season approached. Between October and December, CERT NZ’s Phishing Disruption Service received 1,086 reports of websites impersonating NZ Post. This made NZ Post the most impersonated brand in New Zealand in this period. These phishing messages might also claim to come from other postal companies operating in New Zealand.
How it works
To appear legitimate and credible, scammers like to impersonate well-known brands. The most common way of doing this is to create domains that closely resemble the website of the company they are looking to impersonate.
Phishing messages also seek to create a sense of urgency. A common lure is the use of words like 'track-alert' or 'missed-my-parcel' in the URL path.
Some malicious links hide behind URL-shortening services such as Tinyurl or Bitly.
Why do scammers want your info?
The most common objective for phishing is to harvest credentials. If you enter a password into a fake site, scammers can use that to access your account on the real website or to hack into your other accounts, especially if you use the same password across multiple accounts.
The end goal of scammers is to steal money. Phishing sites will sometimes ask you to make a small payment using your credit card or online banking. While this initial amount appears insignificant, scammers can use the details they have collected for a larger scam in the future.
In many cases, scammers may also try to install malware on your device after you click on these phishing links. The malware could potentially log your activity and collect more information.
How we foil phishing attempts
CERT NZ works to stop phishing campaigns through the Phishing Disruption Service. If you get a phishing text or email, you can submit the URL to the Phishing Disruption Service by sending it in an email to phishpond@ops.cert.govt.nz. CERT NZ collates and verifies the links and sends them out to subscribed organisations which can then block access, preventing the phishing scams from reaching people in the first place.
CERT NZ recommends that organisations set expectations with customers on how you will contact them. For example, promote that you will not send text messages, so if a customer receives a text claiming to be from your organisation,
Watch out for these:
- Check the URL. New Zealand courier companies usually have websites ending in “.co.nz.”
- Some URLS also have the IP as a hostname. This is definitely a red flag. For example http://46.23.1099/
- Messages from overseas phone numbers are most likely a scam.
- If you are expecting a parcel or delivery and you get a message, you can call the postal company to verify.
- Do not give away your information, including your address or sensitive information such as credit card details.
 Insight: Visa-vis
Insight: Visa-vis
While scammers prefer a widespread campaign, hoping to catch anyone who is unaware, they sometimes home in on specific groups they see as susceptible to their messages. We saw a targeted scam of this type in the last quarter of 2023 aimed at Mandarin speakers living in New Zealand on a visa.
Starting in early November, a spate of calls occurred from a source impersonating Immigration New Zealand, telling recipients there were serious problems with their visas.
While calls of this nature - pretending to be from a government agency and targeting people who would interact with that agency - are not new, this particular series was remarkably high in number. CERT NZ and Immigration New Zealand together received over 800 reports across a span of six weeks. Because most incidents go unreported, we estimate the actual number of phone calls to be much higher.
The callers did not start with the knowledge of people’s immigration status or their background. So, while the content of the scam was targeting a certain demographic, anyone with a New Zealand phone number could have received the call.
The nature of the call
This scheme was specifically designed to target Mandarin speakers. The callers masked their originating numbers by 'spoofing' the phone numbers of unsuspecting individuals. The call started with a voice message asking the recipient to choose a language: English or Chinese. Selecting English ended the call. Those who selected Chinese were directed to a scammer who told them that there were issues with their visas and in some cases asked them to return promptly to China.
The callers collected personal and sensitive information (including visa numbers), and sometimes asked for payments to sort out visa problems.
Spoofing is the practice of making your phone number look like a different one. So, even blocking or reporting the number won't work because it's not the real source. Scammers can do this by using cheap and easily available software and the owner of the phone they are spoofing will not know that their number is being used.
Getting the message out
CERT NZ worked with Immigration New Zealand which used its platform and connections to get the message out to people who could be targeted. The Chinese consulate also engaged with us and promptly disseminated information in the community. The number of reports reduced significantly in December and eventually died out, with the last case reported to us on 23 December.
Insight: Adding Insult to Injury – Recovery room scams
Imagine someone who has lost tens of thousands of dollars to an online scam. Soon after, they get a call from an online agency offering to help them get all or most of their money back. The upfront fee of a few thousand dollars sounds like a small amount compared with what the person has lost. But once the fee is paid, the ‘online agency’ goes silent, leaving the victim to realise they have been scammed again.
This is a quintessential recovery room scam, a practice where malicious actors revictimize someone recovering from a hard-hitting scam.
How they work
- Recovery room scams target individuals or organisations that have already been scammed. They may do this by trawling social media or forums for people who post about being scammed.
- In some cases, the same actors responsible for the initial scam may go back to the victim purporting to be someone who can help them with recovering the money they lost. Scammers sell details of their victims to other scammers. These lists contain contact details, the amount lost and the type of scam the person fell for.
- Scammers sell details of their victims to other scammers. These lists contain contact details, the amount lost and the type of scam the person fell for.
- Recovery room scammers will often setup and promote recovery companies online that show up in your search results. These websites look legitimate and it can be hard to recognise them as a scam.
Advice from the Financial Markets Authority
In 2023, the FMA received 36 reports of recovery scams.
“We continue to receive significant reports. While most of the recovery scams are not in our remit as a regulator, we are alarmed by this current trend and feel we need to alert the public,” FMA Senior Responsible Officer Peter Taylor says. “Be very suspicious of anyone who claims they can recover your stolen funds, it’s hard to get your money back once it has been moved offshore. We recommend you talk to your bank if you think you are being scammed this way.”
The FMA recommends the following.
- If you have been the victim of a scam, be on guard against follow-on scams. Also, consider getting a new phone number and email address. It is likely your contact details will be on a scam list.
- Be wary of a company that doesn’t have a physical address or phone number. Note that many scams involve companies using false addresses and telephone numbers. It’s important to verify these against the contact information provided.
- If someone claims to be a government employee, check that the organisation exists. If it does, contact the organisation using the details on its official website and ask to be transferred to the person named in the initial contact to verify that they contacted you. Taking these steps will likely make it clear if it is a scam.
- If you have given anyone remote access to your device and you now suspect it is a scam, disconnect your device from the internet to prevent access.