This quarter, CERT NZ responded to 1,950 incident reports about individuals and businesses from all over Aotearoa. This report shares information about these incidents as well as highlights examples of work CERT NZ is doing to help. There are two parts to the report:
A Highlights Report focusing on selected cyber security incidents and issues.
A Data Landscape Report providing a standardised set of results and graphs for the quarter.
Highlights
The average number of incident reports per quarter is 2,266 and the average direct financial loss is $5 million. These figures are based on the previous quarters. For this quarter (Q2):
$4.2 million in direct financial loss was reported in Q2. 21% of incidents reported financial loss.
1,950 incidents were responded to by CERT NZ in Q2 2023, down 1% from Q1 2023.
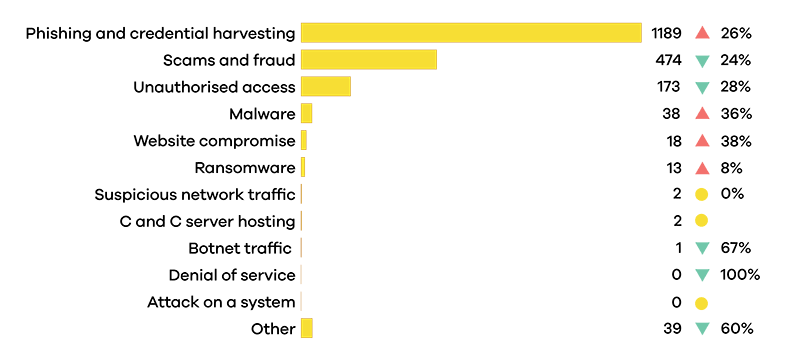
Phishing and credential harvesting reports increased 26% from Q2 2023.
Malware reports increased 36% from Q2 2023.
Number of incidents responded to
A total of 1,950 incidents were responded to in Q2 2023.
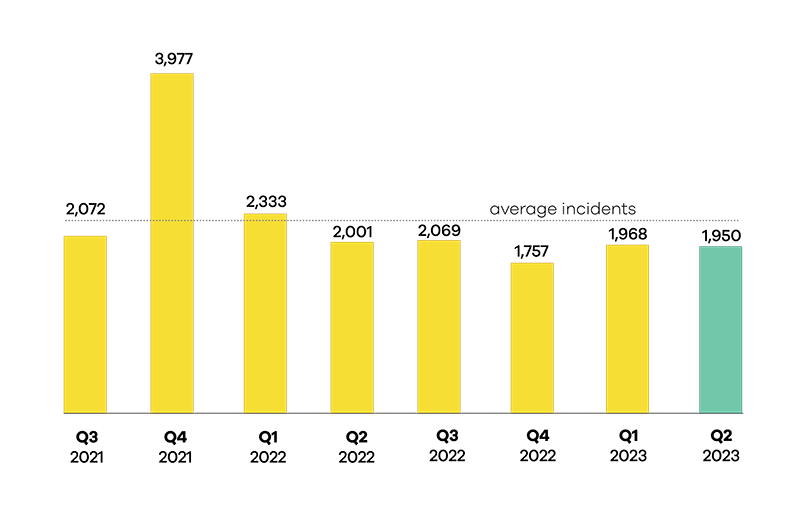
Breakdown by incident category
Phishing and credential harvesting remains the most reported incident category in Q2 2023.
Focus area: Vulnerabilities
Patch work
Online vulnerabilities are constantly being discovered as cyber security actors, both malicious and non-malicious, search for potential 'holes'. This is often when software doesn't run as expected under certain circumstances.
Vulnerabilities can be found in software, hardware, firmware, or online services. Once discovered, they can be exploited to potentially gain access to devices and use that access to do anything from intercepting communications to deploying malware across a network.
 Patch every hole
Patch every hole
When a vulnerability is uncovered, just like a hole in the fence, you need to patch it up. Software owners often release patches intended to reduce or remove the vulnerability.
CERT NZ recommends organisations take the following steps.
- Know what you have running in your system.
- Have a patch management process and update it regularly.
- Where possible, have automatic updates on or update as soon as you can.
Full disclosure
A lot of information about vulnerabilities comes from voluntary and anonymous disclosures. Disclosures allow the affected organisation to work out a solution to the vulnerability before it becomes public and a risk to users.
CERT NZ stresses that disclosure is a good thing, and organisations that supply software or services should have a vulnerability disclosure policy in place.
Without disclosure policies, organisations must rely on their own teams to catch all the holes. If your organisation receives a disclosure, it's good practice to respond to the discloser, where possible, letting them know you have received the notification. This can help you gain clarity on the vulnerability and coordinate further action or publication.
On alert
CERT NZ monitors emerging vulnerabilities that may affect New Zealand businesses and individuals. If we see one that is widespread or being actively exploited that broadly affects New Zealanders, we put out an advisory. Advisories describe exactly which systems the vulnerability affects, the steps needed to identify if you are at risk and how to mitigate or prevent exploitation.
The best way to stay informed is to subscribe to CERT NZ's alerts and advisories.
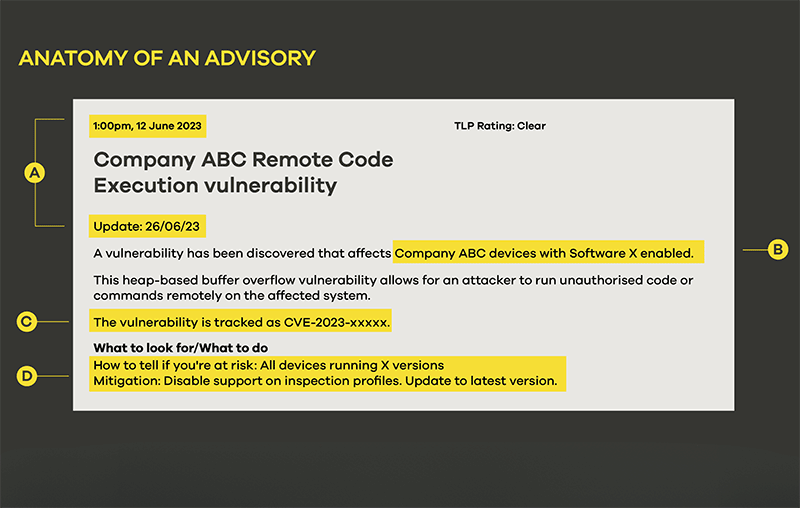
A - Date of publication and date of latest update. Updates may not be sent out to subscribers – though they will be noted on social media – unless the scope of the vulnerability has widened significantly, or the vulnerability is in active use by malicious actors.
B - The affected systems will be listed in the introduction with more detail.
C - The Common Vulnerability and Exploit (CVE) code for the vulnerability. This means the vulnerability has been added to the CVE database. CERT NZ will sometimes send out advisories on 'zero-day' vulnerabilities that are too new for a CVE code.
D - The 'What to look for' and 'What to do' section provides details to help you work out if you're at risk along with providing prevention and mitigation advice.
The advisory will have a list of affected software and firmware versions or, if the vulnerability requires a combination of factors, it will outline these. A section is included on mitigation and, where possible, prevention. The last section includes further information and links to any available patches or updates.
Case study
CERT NZ's proactive outreach happens when it identifies a vulnerability that directly affects a small number of organisations. (We have removed identifying details.)
 Through monitoring, CERT NZ identified a newly discovered vulnerability that was high risk because of the level of impact a breach could have.
Through monitoring, CERT NZ identified a newly discovered vulnerability that was high risk because of the level of impact a breach could have.
 CERT NZ identified that only a handful of New Zealand services would be vulnerable.
CERT NZ identified that only a handful of New Zealand services would be vulnerable.
 CERT NZ contacted the organisations and provided advice on mitigation.
CERT NZ contacted the organisations and provided advice on mitigation.

The organisations applied the mitigation and continued to monitor the situation.
 Over the next few days, reports began circulating that the vulnerability was actively being used by ransomware groups.
Over the next few days, reports began circulating that the vulnerability was actively being used by ransomware groups.
In some instances, the vulnerability may change over time to include more affected systems than originally reported. When this happens, we work quickly to put out an advisory (or update) and make sure any organisations at risk put mitigations in place as soon as possible.
Insight: SMS phishing
Gone smishin'
It's something many people consider an annoyance, however, phishing remains the largest reporting category to CERT NZ and one of the biggest paths for other types of attacks.
 Historically, most phishing was delivered by email. However, this year, CERT NZ has seen many more phishing text messages (also known as 'smishing') than phishing emails.
Historically, most phishing was delivered by email. However, this year, CERT NZ has seen many more phishing text messages (also known as 'smishing') than phishing emails.
The risks to people are increased with smishing because most people have their phones on them all the time and see text messages as soon as they arrive. This means messages can come through at times when you aren't thinking as clearly. Links sent via text messages are also easy to disguise using URL shorteners (for example, bit.ly) and can be sent from 'spoofed' phone numbers.
While the exact wording will change, typically, smishing messages pretend to be from a reputable organisation: banks, Inland Revenue, New Zealand Post, Waka Kotahi and other government departments. They usually claim there is an issue and ask you to click on a link to resolve it. A sense of urgency is often included around the action.
Recently, some smishing texts have come with a phone number as well as or instead of a link. Calling the number gives the scammers direct access to you and can make their scam seem more legitimate.

Advice
The best way to keep yourself safe from these scam messages is not to click on links in text messages and emails. Even if you think the text might be legitimate, it's better to navigate to the organisation's website using another method.
Insight: Online marketplace scams
Ghosted in the marketplace
Everyone loves a good online marketplace. Unfortunately, they are also a great place for scammers to find potential targets.
In the last quarter, CERT NZ received reports of specific tactics scammers use in these marketplaces.

Reverse pickup scam
In this situation, the scammer poses as a buyer and pretends to purchase an item from a genuine seller. The scammer says they have prepaid for a courier to pick up the item and asks the seller to send them an 'insurance fee' they will refund when the item arrives. The fee is what the scammer wants.
 The scammer may threaten to report the target, to get them to pay. After they receive the fee, they will break off all contact with the seller and cancel any purchase they may have agreed to. It can be hard to recover any funds from this type of scam simply because it requires a lot of work and back-and-forth between banks and the marketplace.
The scammer may threaten to report the target, to get them to pay. After they receive the fee, they will break off all contact with the seller and cancel any purchase they may have agreed to. It can be hard to recover any funds from this type of scam simply because it requires a lot of work and back-and-forth between banks and the marketplace.

 Bank account limit scams
Bank account limit scams
This is a sneakier scam. Again, the scammer claims to be interested in purchasing an item from a genuine seller. They request bank account details from the seller to make the payment. The scammer then asks the seller to check their email for confirmation of payment.
The email looks to be from the seller's own bank and claims that a transaction was attempted but couldn’t be processed due to a limit on their bank account. The scammer is the one who sent the email, and it states your 'bank account limit' can be increased by transferring your last buyer (the scammer in this case) a certain amount of money, which will be refunded to you once your limit has been increased.
Again, when the target sends through the money, the scammer immediately breaks off all communications and leaves the legitimate seller out of pocket and with a long fight to recover any of the funds.
![]()