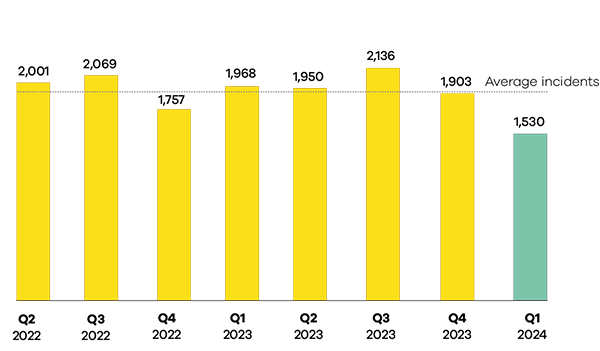
This quarter, CERT NZ responded to 1,530 incident reports about individuals and businesses from all over Aotearoa. This report shares information about these incidents as well as highlights examples of work CERT NZ is doing to help. There are two parts to the report:
A Highlights Report focusing on selected cyber security incidents and issues.
A Data Landscape Report providing a standardised set of results and graphs for the quarter.
$6.6 million in direct financial loss was reported in Q1, up 84% from Q4 2024. 19% of incidents reported financial loss.
1,530 incidents were responded to by CERT NZ in Q1 2024, down 20% from Q4 2023.
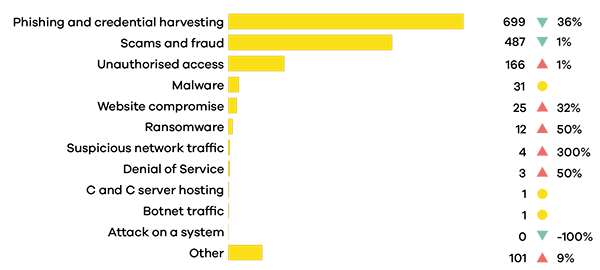
The biggest drop in number of reports was in the Phishing and Credential Harvesting category which saw a 40% decrease on Q4 2023.
Scams while buying or selling goods online went up by 15% from 214 in the previous quarter to 247 in Q1 2024.
A total of 1,530 incidents were responded to in Q1 2024.
Phishing and Credential Harvesting remains the most reported incident category in Q1 2023 despite a 36% drop in the number of reports.
Focus Area: Battling Breaches
Data breaches are a significant concern for organisations of all sizes and their clients and customers.
A data breach occurs when an unauthorised person gets access to information they shouldn’t have. This can include anything from names and email addresses to credit card details, passwords, and intellectual property.
How it happens
Data breaches can happen because of an intentional attack or unintended error.
- Cybercriminals can exploit vulnerabilities in systems or networks to access your data.
- Someone in your organisation may be targeted in a phishing attack and tricked into revealing important information, such as their login details.
- Insider threats can be a source of a data breach. Anyone with authorised access could misuse their privilege or intentionally leak information.
- Data can also be leaked through human error, such as in an email to the wrong person, or through misplaced or stolen devices containing sensitive information.
Effects of a breach
A data breach can affect your organisation in many ways.
 Drum up your defences
Drum up your defences
Good security practice is your best defence against potential attacks. Add layers of protection around the data you store to protect it from those who try their best to get their hands on it.
Case Study: James and the Giant Breach
James* is the IT manager of a shoe and clothing store chain called Centipod*, which has 40 employees across eight stores in New Zealand. He is alerted to a post on an online forum threatening to sell his company data, with the attacker claiming that 10,000 records are available. James realises that someone has gained unauthorised access to the database of the store’s customers.
His next actions will be crucial in deciding how the company meets this challenge. James has had previous experience of a data breach and he takes the following steps.
 Insight: A report on reports
Insight: A report on reports
Nearly all of CERT NZ's information comes from the general public – people like you.
When businesses and individuals report online incidents to us, we know what scam and malware campaigns are affecting New Zealand. In this way, every report not only helps you, but all Kiwi.
You can report any cyber incident confidentially. If you're locked out of your accounts, suspect you have been targeted in a scam, or if your organisation suffers a data breach, you can report it to us using the reporting tool on CERT NZ’s website.
Handling reports
CERT NZ works with partner agencies, like the New Zealand Police, the Department of Internal Affairs, banks and telecommunication companies. If you need more help, and consent to it, we can forward your report to these agencies.
You don’t have to experience an incident online to talk to us. If you think you or someone you know is being targeted in a scam, CERT NZ can provide technical advice.
What’s happening behind the scenes?
Almost half of the reports we receive are about phishing. Domains and URLs that are verified as phishing links get listed on CERT NZ’s Phishing Disruption Service (PDS). Organisations such as cyber security service providers who are subscribed to the PDS can block access to these domains so no one in the organisation they serve can get to the sites.
CERT NZ also sends takedown requests to service providers that host these domains. Often, these providers are based overseas. If they comply with our request, the website gets taken down and can’t be used to scam other New Zealanders.
But we cannot stop online attackers from creating a new domain or website and starting over again. We are alerted to these new domains when you report to us and the cycle repeats.
 Insight: A case for passkeys
Insight: A case for passkeys
You might have heard some of the most popular phone apps are switching to or enabling passkeys to make logging in easier and more secure.
Passkeys are a way of logging in without passwords. They use something you have (like a USB key or your phone), or recognise who you are with your face scan, voice or fingerprint, to let you into your account. You may already have apps on your phone, such as your digital wallet, that use this form of authentication.
What happened to passwords?
Passwords are the most popular tool for authentication. But scammers are always trying to get their hands on them, and their jobs are made easier when people don't have strong passwords or use the same password for multiple accounts.
That’s where passkeys have an advantage. Passkeys are device-specific, and your data is not saved on a website server. So even if the website suffers a data breach, scammers can’t steal your credentials.
Are passwords history?
Not quite. Passwords are handy and if done right, they can be a strong line of defence. If you use long and unique passwords, attackers can’t brute force their way into your account. CERT NZ strongly advises enabling two-factor or multi-factor authentication on your most important accounts, such as banking, email and social media, to make them more secure.
Use two-factor authentication to protect your accounts External Link
Most sites and apps that let you use a passkey also require you to have a backup password that helps you recover your account. Not all devices can perform face or fingerprint scans, or take external keys, so passwords remain the most common method of verifying user identity. CERT NZ has a guide on creating good passwords and protecting your online accounts.
Create good passwords External Link
The upside
- Using passkeys can make logging in faster.
- You don’t have to create, or remember, complex passwords.
- Passkeys are phishing-resistant – scammers cannot remotely log in to your account with a password because there is none.
The downside
- If you lost access to all your devices at once, it can be difficult to enter your own account.
- Biometric logins don’t always work and may need you to use your password. For example, when trying to use a finger scan with greasy or wet fingers, or a face scan in the dark.
- Devices that read fingerprints or can recognise face scans can be more expensive. If you use an external key or a second device for authentication, that is an additional cost as well.
Sign up to the quarterly newsletter to receive CERT NZ’s reports and updates.