This quarter, CERT NZ received 2,097 incident reports about individuals and businesses from all over New Zealand. This report shares examples of the incidents and advice on how to best protect against them.
There are two parts to the report:
- A Highlights Report focusing on selected cyber security incidents and issues.
- A Data Landscape Report providing a standardised set of results and graphs for the quarter.
Highlights
2,097 incidents were reported in Q4, down 20% from Q3.
$2.8 million in direct financial loss was reported in Q3, with 14% of incidents reporting associated financial loss.
41% of all reports were about phishing and credential harvesting.
30% of all reports were about malware, making it the second highest incident category.
The average number of incident reports per quarter is 1,473 and average direct financial loss is $4.6 million. These figures are based on the previous eight quarters.
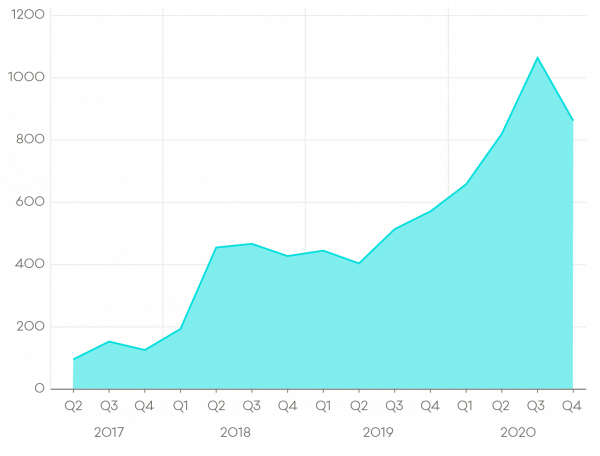
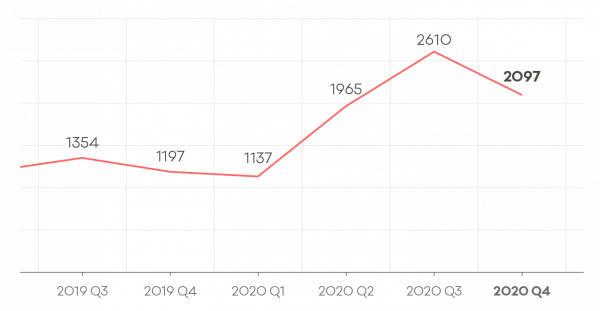
Number of incident reports by quarter
A total of 2,097 incidents were reported in Q4, down 20% from Q3.
Full breakdown of incident reports for Q3 2019 to Q4 2020:
- Q3 2019: 1,245
- Q4 2019: 1,197
- Q1 2020: 1,137
- Q2 2020: 1,965
- Q3 2020: 2,610
- Q4 2020: 2,097
Breakdown by incident category
Phishing and credential harvesting remains the most report incident category.
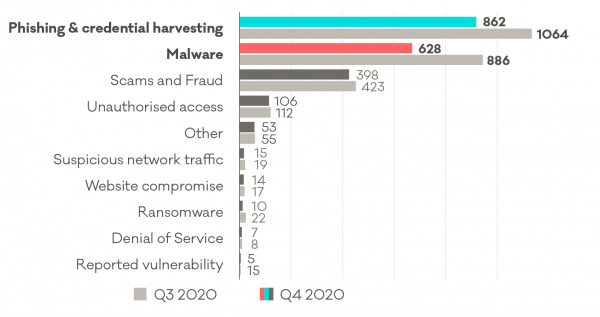
| 2020 Q4 | 2020 Q3 (Comparison) | |
| Phishing & credential harvesting | 862 | 1064 |
| Malware | 628 | 886 |
| Scams and fraud | 398 | 423 |
| Unauthorised access | 106 | 113 |
| Other | 53 | 55 |
| Suspicious network traffic | 15 | 19 |
| Website compromise | 14 | 17 |
| Ransomware | 10 | 22 |
| Denial of service | 7 | 8 |
| Reported vulnerability | 5 | 15 |
Phishing
Phishing incidents
Phishing is consistently one of the highest incident categories reported to CERT NZ – making up 41% of all incidents reported in Q4, 2020.
Phishing trends in Q4
Attackers use a variety of phishing techniques to try and trick recipients into sharing their private information, making financial transactions, or opening malicious attachments or files.
Protect yourself from phishing
Attackers use different techniques to try and trick people in to sharing their information. These steps will help you shore up your online defences.
Malware
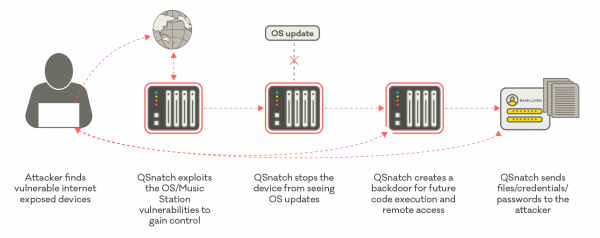
Malware targeting network attached storage devices
Attackers use a variety of techniques to spread malware and get their hands on private information.
In some cases they send malicious software through email attachments or links to infect recipient’s computers, in other cases, they target specific internet-exposed services.
If you think your device has been affected, please report to CERT NZ www.cert.govt.nz/report
Data breaches
Risk of data breaches continue to rise
In Q4, the number of vulnerable databases continued to rise, up 26% from Q3.
Databases are a target for attackers because they often hold all sorts of private information. If a database is openly accessible from the internet, attackers can easily access the information it holds, and use it for financial gain. For example, the attacker may threaten to leak the data unless a ransom is paid or sell it to other attackers.
Protecting from a data breach
While you may need to engage your IT provider to secure your database, reducing the risk of a data breach is easier than fixing one. CERT NZ recommends the following steps:
- Make sure your databases are not exposed to the internet.
- Make sure your systems have the latest security updates.
- Use long, strong and unique passwords.
- Develop an incident response plan for what to do if your business is affected by a data breach.
Creating an incident response plan
- Only collect information that you actually need from your customers and be clear about why you need it, as stated in the Privacy Act 2020.
Case study: CERT NZ helps New Zealand business secure databases
In Q4, the CERT NZ team identified that 23 seemingly individual Microsoft SQL servers were all linked to one nationally-franchised retail business. All servers were running a variety of versions and were served by a number of ISPs. These potentially vulnerable systems appeared to include back office and point of sale systems.