This quarter, CERT NZ responded to 1,757 incident reports about individuals and businesses from all over New Zealand. This report shares information around these incidents as well as highlighting examples of work CERT NZ is doing to help. There are two parts to the report:
A Highlights Report focusing on selected cyber security incidents and issues.
A Data Landscape Report providing a standardised set of results and graphs for the quarter.
Highlights
The average number of incident reports per quarter is 2,124 and average direct financial loss is $4.6 million. These figures are based on the previous quarters.
$3.5 million in direct financial loss was reported in Q4. 26% of incidents reported financial loss
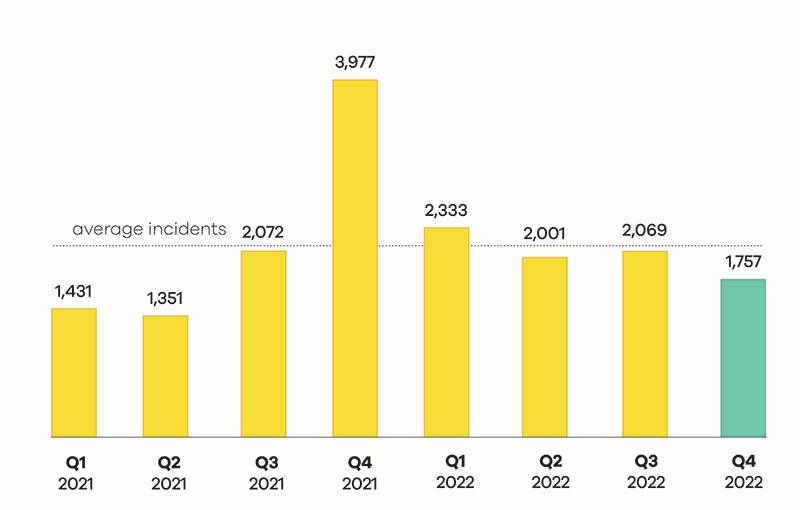
1,757 incidents were responded to by CERT NZ in Q4 2022, down 15% from Q3 2022
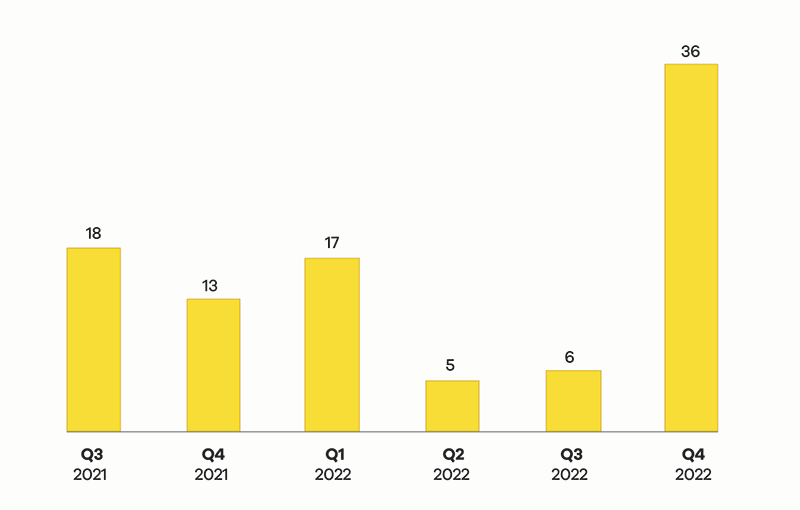
Ransomware reports increased 500% from Q3 2022.
10% increase in malware reports from Q3 2022
Number of incidents responded to
A total of 1,757 incidents were responded to in Q4 2022
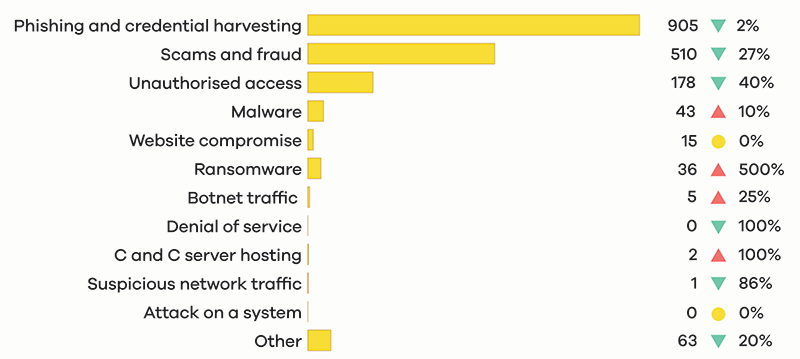
Breakdown by incident category
Phishing and credential harvesting remains the most reported incident category
Focus area: Ransomware
Held to ransom
Reports of ransomware attacks over the last two years have tended to wax and wane. However, in Q4 of 2022 the numbers increased suddenly month on month, to the highest numbers CERT NZ has received in a quarter.
In part, this is the effect of an attack on one company that had downstream effects on others. This is covered further below.
There is no one type of business that is more susceptible to ransomware. Reports to CERT NZ show that the attacks are spread out across a range of organisations. This could potentially be because attackers are looking for certain systems, legacy devices or exploitable vulnerabilities, rather than targeting specific businesses.
How a ransomware attack happens and what you can do to stop it
A typical ransomware attack has three parts: initial access, consolidation and preparation, and impact on target. Knowing how an attacker works can help you know what to do to stop them.
 Initial Access
Initial Access
First an attacker needs to get access to your system, so this is also your first line of defence.
Attackers have a few ways to try and get in, but the most common ones are phishing for credentials, collecting compromised passwords found in data breaches, using software to “brute-force” guess passwords, exploiting a software vulnerability, or tricking a user into downloading malware.
Consolidations and preparation
 After gaining access, an attacker then deploys tools to take control and spread further through the system. They will attempt to access all devices and parts of your system, including back-up servers. During this stage, the attackers will be trying to hide their activities, doing things like disabling security controls and working outside of regular office hours.
After gaining access, an attacker then deploys tools to take control and spread further through the system. They will attempt to access all devices and parts of your system, including back-up servers. During this stage, the attackers will be trying to hide their activities, doing things like disabling security controls and working outside of regular office hours.
Impact on target
Once they are in a system and have their tools running, the attacker can do what they want. This can include stealing (exfiltrating) data to sell or hold to ransom, as well as encrypting your system and destroying backups.
Your best bet at this point is to have an incident response plan and, if possible, a robust and well-tested backup to restore to. As attackers will attempt to delete your backups, keeping them offline or disconnected from your internetconnected servers is critical.
If you discover an attacker in the early stages, you may need to move carefully as they could trigger a lockdown early to prevent you from removing or disabling their tools.
If you suffer an attack
In the event of an attack, you will need to implement your incident response plan. If you don’t have one, CERT NZ has resources to help create it. Reporting the incident as soon as possible to CERT NZ will mean we can help you in your response.
 Crashing the third party
Crashing the third party
With businesses needing more IT and online services, there has been a rise in third-party software as a service (SaaS) and managed service providers. This can range from server hosting to the running of full IT systems remotely.
This gives organisations the ability to outsource a lot of technical work while keeping costs down. However, that makes these external services a target for attackers as it potentially gives them access to all the connected organisations.
How to mitigate this
When looking for a supplier, ensure you go over your own certification and accreditation process with them. Ask to see incident response plans and review their controls (such as those mentioned in the Focus Area on ransomware). Larger suppliers may be less vulnerable, but no one is 100% protected. Backups are essential so, ensure that they are offsite or disconnected.
If you are affected
![]() If you use a third-party supplier and they get hit with an attack, such as ransomware, there isn’t much you can do.
If you use a third-party supplier and they get hit with an attack, such as ransomware, there isn’t much you can do.
![]() Contact CERT NZ and we can help work with the supplier. They should be in contact with you as soon as they learn of the attack and report any potential breaches or lost information. You will need to communicate with your stakeholders and possibly the Office of the Privacy Commissioner.
Contact CERT NZ and we can help work with the supplier. They should be in contact with you as soon as they learn of the attack and report any potential breaches or lost information. You will need to communicate with your stakeholders and possibly the Office of the Privacy Commissioner.
![]() There is also the chance that the attackers will double down, and use the information stolen from the supplier to target its clients directly or move even further downstream to attack those connected to the clients.
There is also the chance that the attackers will double down, and use the information stolen from the supplier to target its clients directly or move even further downstream to attack those connected to the clients.

Insight: Blackmail scams
Fake extortion leads to real losses
We’ve seen blackmail/extortion campaigns in Aotearoa before. Peaking in Q2 of 2020, with 482 reports which made up almost a quarter of every report to CERT NZ.
The reports for extortion have tailed off but we’re still seeing roughly one every three days (186 reports in 2022)
What is extortion and blackmail?
In a cyber context, extortion scams take the form of an email trying to trick recipients into paying money by threatening to release private information or images. Although these emails can be frightening to receive, the threats are frequently opportunistic and not credible.
Scammers use urgency and authority
These sorts of scams are designed to create stress and fear in the targets. The scammers use urgency to push these emotional buttons – for example, a short deadline for payment. They also pretend to have authority, by using technical language and talking like experts despite their claims not standing up to further scrutiny.
Reports from 2022 have included the following claims from scammers
- They have hacked your email and installed malware on your computer. Possibly controlling your computer’s camera or keyboard. To add weight to the scam, the scammers can make it look as though the message has been sent from your own email address.
- They have recorded video of you via your computer’s webcam. They will usually say this footage is of you in compromising positions or visiting adult websites.
Previously these sorts of scams included a password you’ve used for an online service to make their extortion seem more plausible. The scammer gets this password from data breaches of the different online service.

What to do if you receive an extortion email
If you receive an extortion email:
- do not respond,
- do not pay, and
- report them to CERT NZ.
Reports to CERT NZ are completely confidential and are treated with care as we know these threats can be shocking to receive, even if they aren’t credible.
If the scammers included a password in the email, make sure to go to any accounts where that password is used, change it and, if possible, enable two-factor authentication.
