Ransomware goals and trends
Ransomware is a financially motivated cybercrime, where the individuals and organisations responsible are well-resourced and increasingly sophisticated. Attacks are growing in number, with recent high profile incidents resulting in payments of multi-million dollar ransoms to recover encrypted data. As the profitability of these criminal enterprises is driving the increase in these attacks, CERT NZ recommends never paying a ransom as doing so helps fund this criminal ecosystem.
The Government has also released guidance on cyber ransom payments, partically for government agencies.
Cyber ransom advice External Link
Ransomware attackers continue to evolve their techniques and operations. As part of their operation they work to understand the business they have compromised. This is so they can demand the largest ransom they believe an organisation will be willing to pay and distribute their efforts compromising networks based on expected payoff.
For example they will often carry out their operation at times where staff of the affected organisation are sleeping, in order to reduce the likelihood that they will be detected or disrupted. In many cases, the first sign of a ransomware incident is a lock screen or note left on devices saying data has been encrypted and a payment is being demanded.
How does ransomware happen and how you can protect against it?
There are a number of ransomware attackers and variants, each with different approaches and tactics. By looking at these attacks collectively, we can see there are commonalities and several opportunities for organisations to detect, prevent, and respond to ransomware attacks before your data gets encrypted. Focusing too heavily on a single attacker or variant will lead to overly narrow defences and may leave you vulnerable to different tactics and techniques.
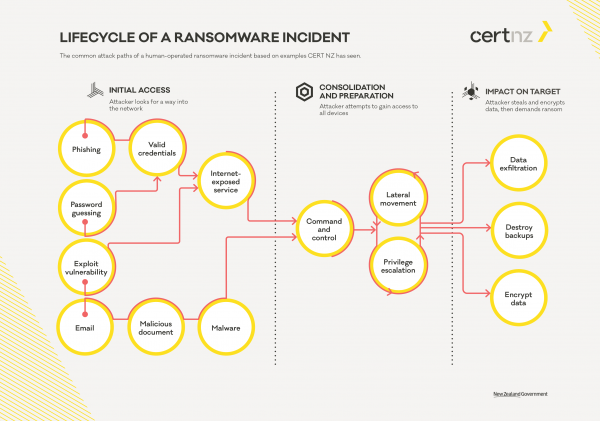
The common attack paths of a human-operated ransomware incident based on examples CERT NZ has seen
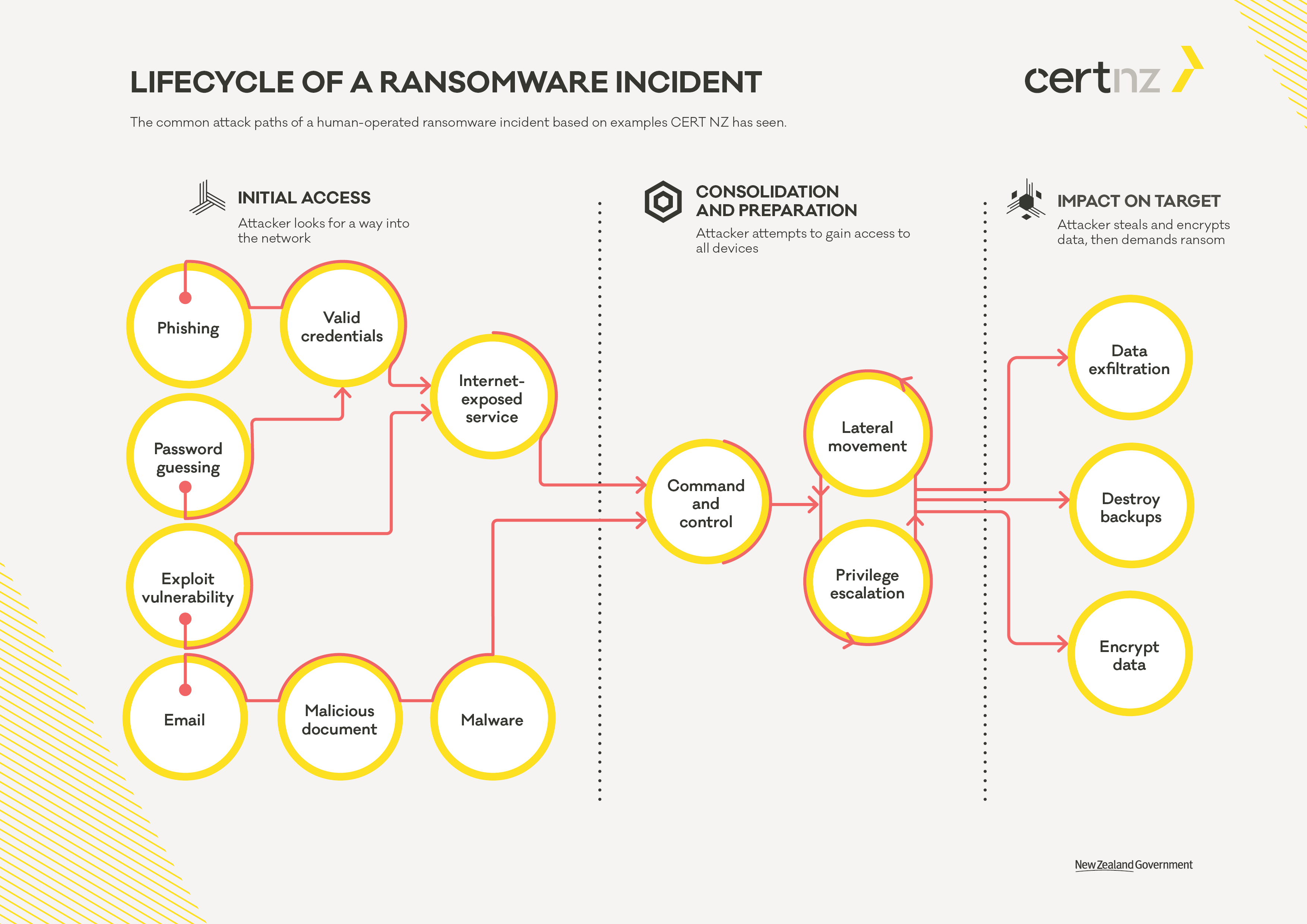
Lifecycle of a ransomware incident [PDF, 29 KB]
We break a ransomware incident into three phases:
In each phase different attackers use different tools and techniques, but the goals of each attacker remain the same. By understanding the goal of the attacker, we can refine our defences to make it harder for them to achieve, it regardless of which tools or ransomware variant you’re dealing with. It’s important not to rely on a single security control and take a defence-in-depth approach. An incident response plan should be prepared ahead of time taking into consideration how you would respond and recover from a ransomware incident.
To help prepare your defences we’ve mapped our critical controls along various stages on the lifecycle of a ransomware incident. This will help identify potential gaps in your defences and make sure the implementation of the critical controls gives you the best chance of stopping a ransomware attack before it’s too late.
We have have created a visual representation of the lifecycle of a ransomware attack focusing on the most common pathways we see in reported ransomware incidents. It’s not an exhaustive description of every possible pathway but serves as a start for you to plan your defences.
How the CERT NZ critical controls can help you stop a ransomware attack in its tracks
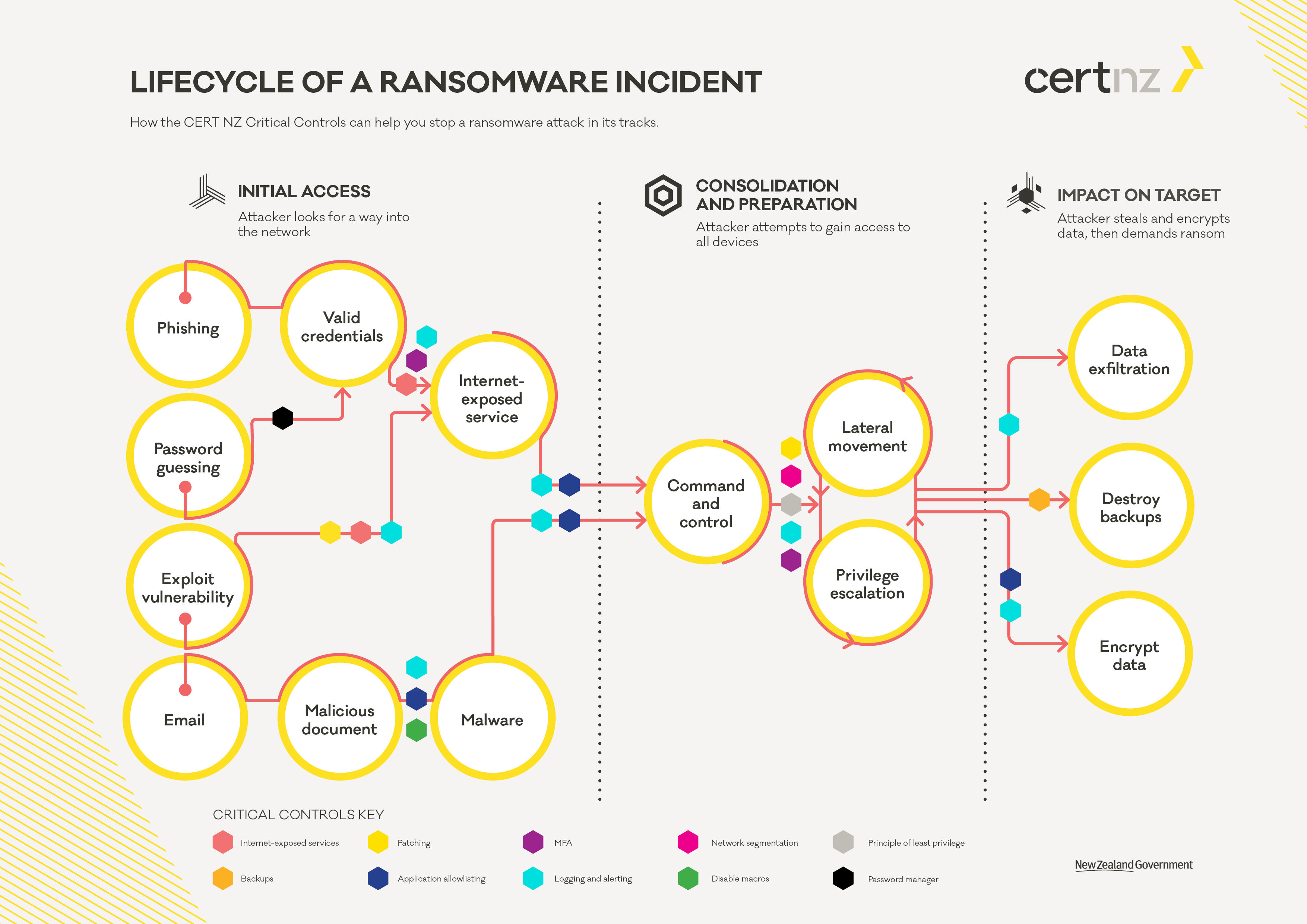
Lifecycle of a ransomware incident (with controls) [PDF, 29 KB]
As you can see, no single tool or control can prevent a ransomware attack on its own. A defence-in-depth application of the critical controls provides a strong defensive net to detect, prevent and respond to any potential ransomware attack before your data is encrypted.
For more in-depth information about defending against ransomware in all phases of the attack, along with MITRE ATT&CK® references, there’s a page about each phase detailing individual parts of the attack and how the critical controls can prevent an attacker from achieving their goals.
ATT&CK® references and examples of commonly used or targeted tools and technologies are not an exhaustive list of every tactic, technique or process used by attackers. This information is provided to give you a basis to verify your defences, highlighting the characteristics we most commonly see.
ATT&CK® is a registered trademark of The MITRE Corporation