COVID-19 disrupted the activities of all New Zealand businesses and organisations this year. For CERT NZ, it meant the production of the 2020 Q1 report was interrupted. That's why this publication provides a half year picture of the data and trends in 2020, rather than the usual quarterly focus.
There are two parts to the report:
- A Highlights Report focusing on selected cyber security incidents and issues.
- A Data Landscape Report providing a standardised set of results and graphs for the quarter.
Quarterly Report: Highlights Q1 & Q2 2020 [PDF, 454 KB]
Quarterly Report: Data Landscape Q1 & Q2 2020 [PDF, 2.4 MB]
Accompanying the report is the 2020 Half Year Summary, giving an overview of what CERT NZ has seen and done in 2020.
Q1 and Q2 highlights
Incident reports
Q1 reports 1,137
Q2 reports 1.965
Total 3,102 reports for Q1 and Q2
73% increase in reports from Q1 to Q2
42% increase in reports on 2019
$7.8 million total financial loss reported
Increases and decreases on 2019
Phishing and credential harvesting
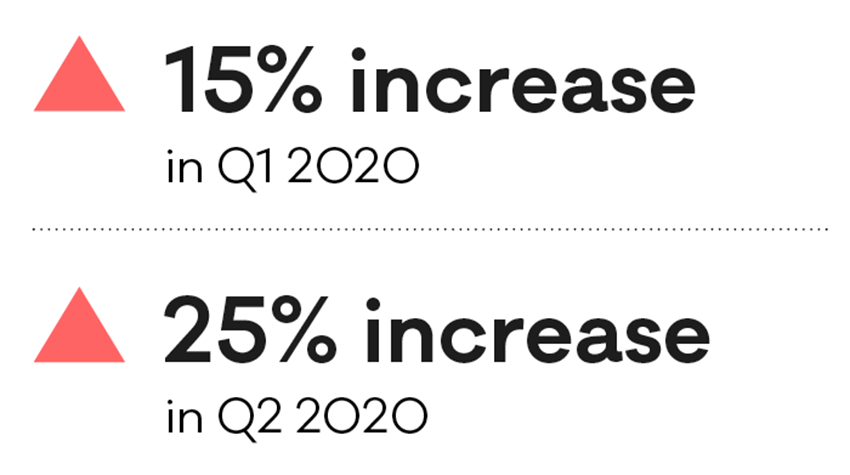
Scams and fraud
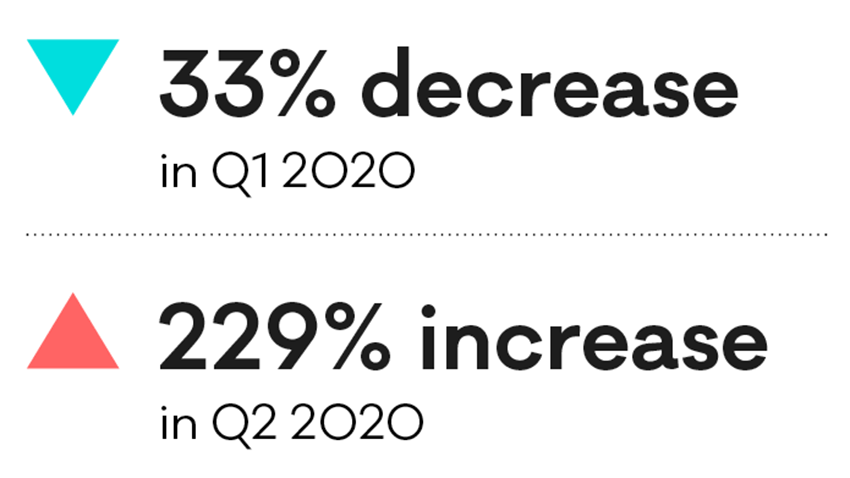
Incident reports by quarter 2019 – 2020 (year to date)
A total of 3,102 incidents reports were received in Q1 and Q2 2020. There was a 73% increase in incident reports from Q 1 to Q2 2020.
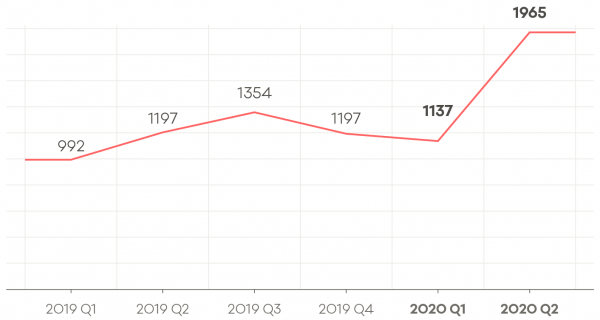
Full breakdown of indicent reports for 2019 Q1 to 2020 Q2:
- 2019 Q1: 992
- 2019 Q2: 1197
- 2019 Q3: 1245
- 2019 Q4: 1197
- 2020 Q1: 1137
- 2020 Q2: 1965
Financial loss
Total financial losses were $7.8m for Q1 and Q2 collectively.
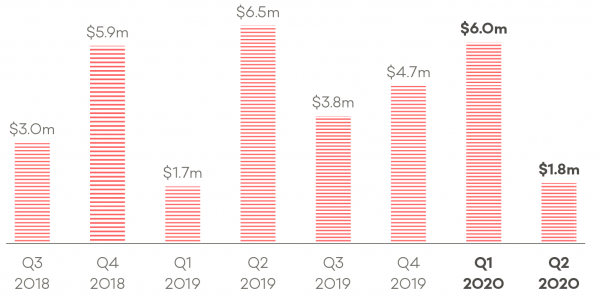
Full breakdown of financial loss for 2018 Q3 to 2020 Q2:
- 2019 Q3: $3.0m
- 2018 Q4: $5.9m
- 2019 Q1: $1.7m
- 2019 Q2: $6.5m
- 2019 Q3: $3.8m
- 2019 Q4: $4.7m
- 2020 Q1: $6.0m
- 2020 Q2: $1.8m
Scam and fraud reports
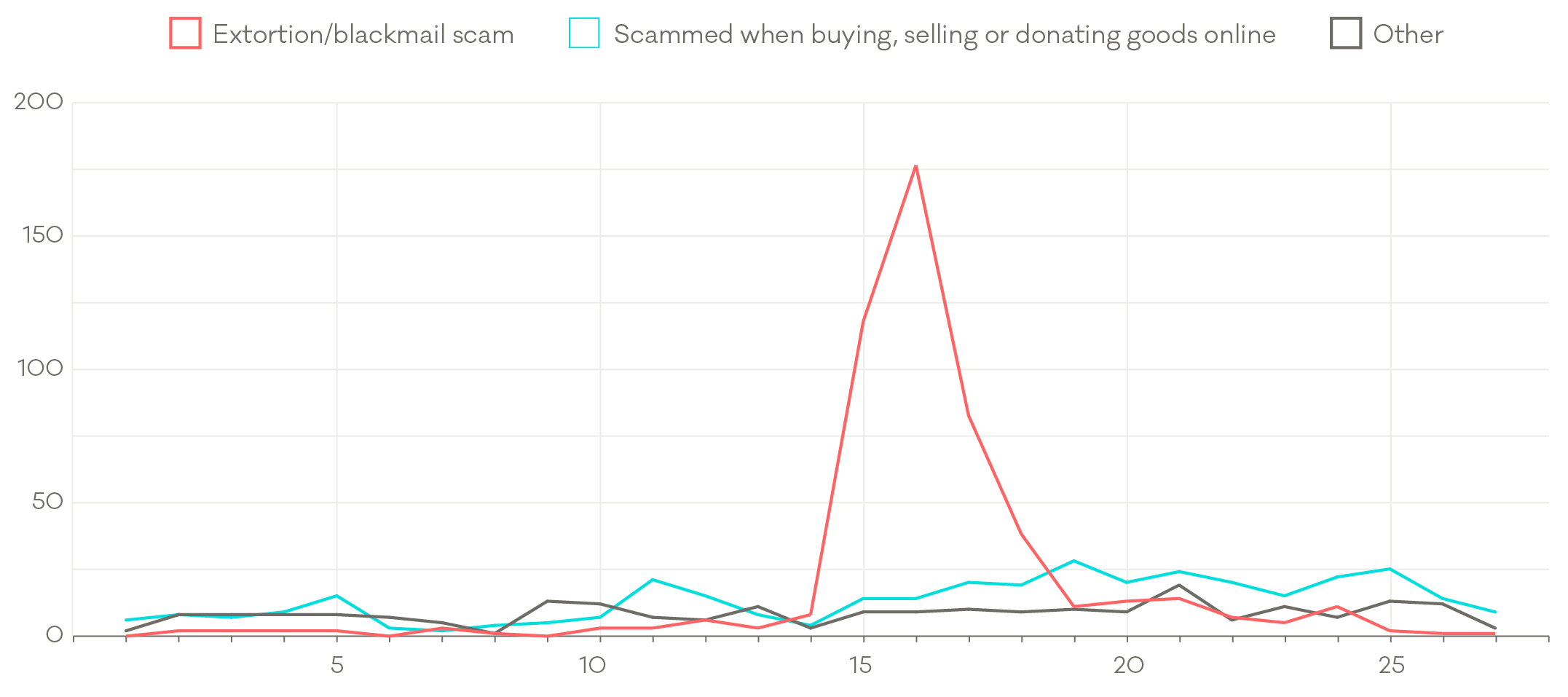
- Increase in reports of web cam extortion emails in Q2 – 478 in that quarter, up from 34 in Q1
- 119% increase in online trading scams during Q2 – from 112 in Q1 to 246 in Q2
If you have experienced a cyber security issue, report it to CERT NZ .
For more on the New Zealand threat landscape in Q1 and Q2 2020, See the CERT NZ Quarterly Report: Data Landscape [PDF 2.4 MB] [PDF, 2.4 MB].
Focus area: Multi-stage malware threats
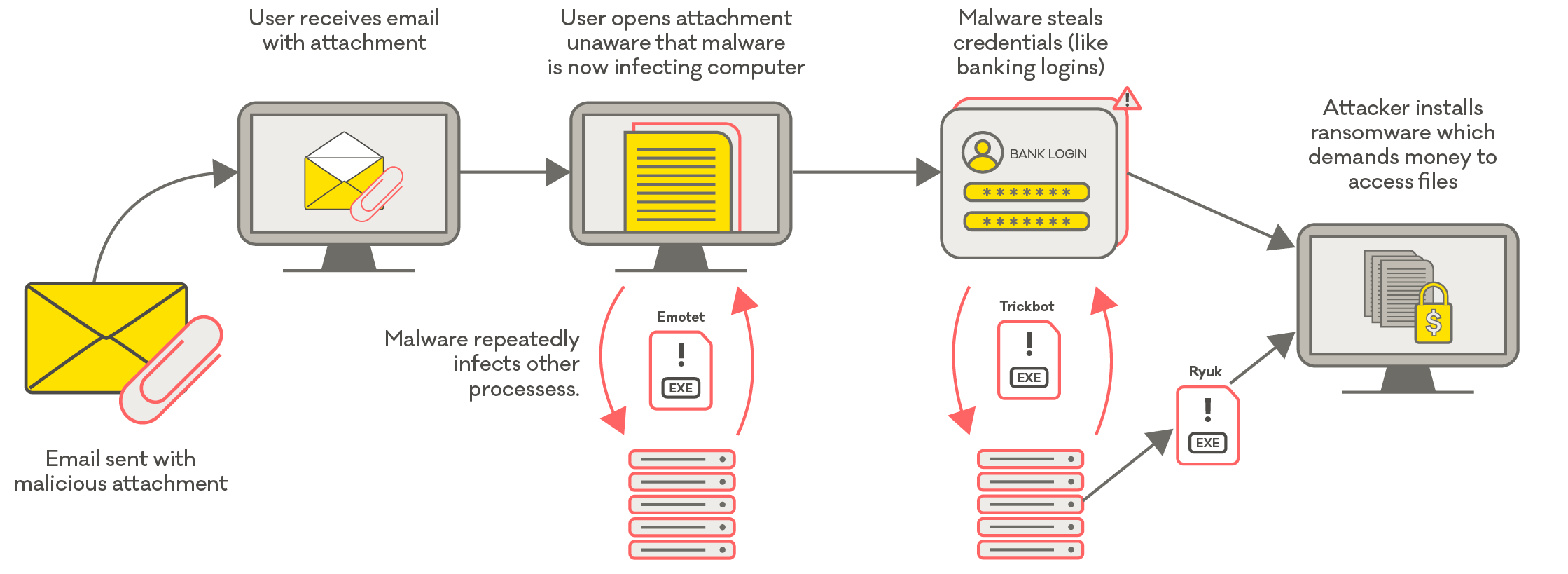
Overview
Malware compromises are some of the most serious cyber security threats we deal with at CERT NZ. By its very nature, most malware aims to go unnoticed, which is why we often speak with people who have discovered all too late that they've been compromised. Many people only become aware of an attack after they've experienced harm from data loss, breached privacy, files held for ransom and credential thefts (leading to money being stolen).
In some cases we receive information from our partners with evidence of malware compromises before they have been detected by the end user. In these cases, CERT NZ immediately contacts the affected parties to inform them of the compromise. We then help them secure their accounts, remove the infection and put systems in place to safeguard against future threats.
We received 46 reports of malware incidents in Q1 and 2 2020 - a 20% increase on the 41 received in Q3 and 4 2019. Here's a look at two cases we've handled so far in 2020.
Qakbot
A malware variant known as Qakbot (also known as Qbot) has been observed globally since around 2007. It's used for cybercrime campaigns that steal sensitive information, like banking credentials, from infected users. Typically circulated via malicious email attachments, Qakbot is designed to evade anti-virus detection, infect computers and steal sensitive credentials stored in the systems they inhabit.
Ryuk
Trickbot/Ryuk is an interesting ransomware variant. According to security firm CrowdStrike, 'Ryuk is specifically used to target enterprise environments'2. It is often installed on systems that have already been compromised with other criminal malware like Trickbot.
Preventions and mitigations
Malware is easier to avoid, than to fix. Implementing CERT NZ's critical controls will help organisations protect themselves from much of the malware circulating. The following controls are particularly relevant to preventing malware attacks:
- Patching (updating) your software and system
- Implementing and testing backups
- Enforcing the principle of least privilege
- Implementing network segmentation
Some key malware terms
Malware can be complicated! Particularly when talking about variants, families, stages and types. Some of the key things you need to know when talking about malware are included below.
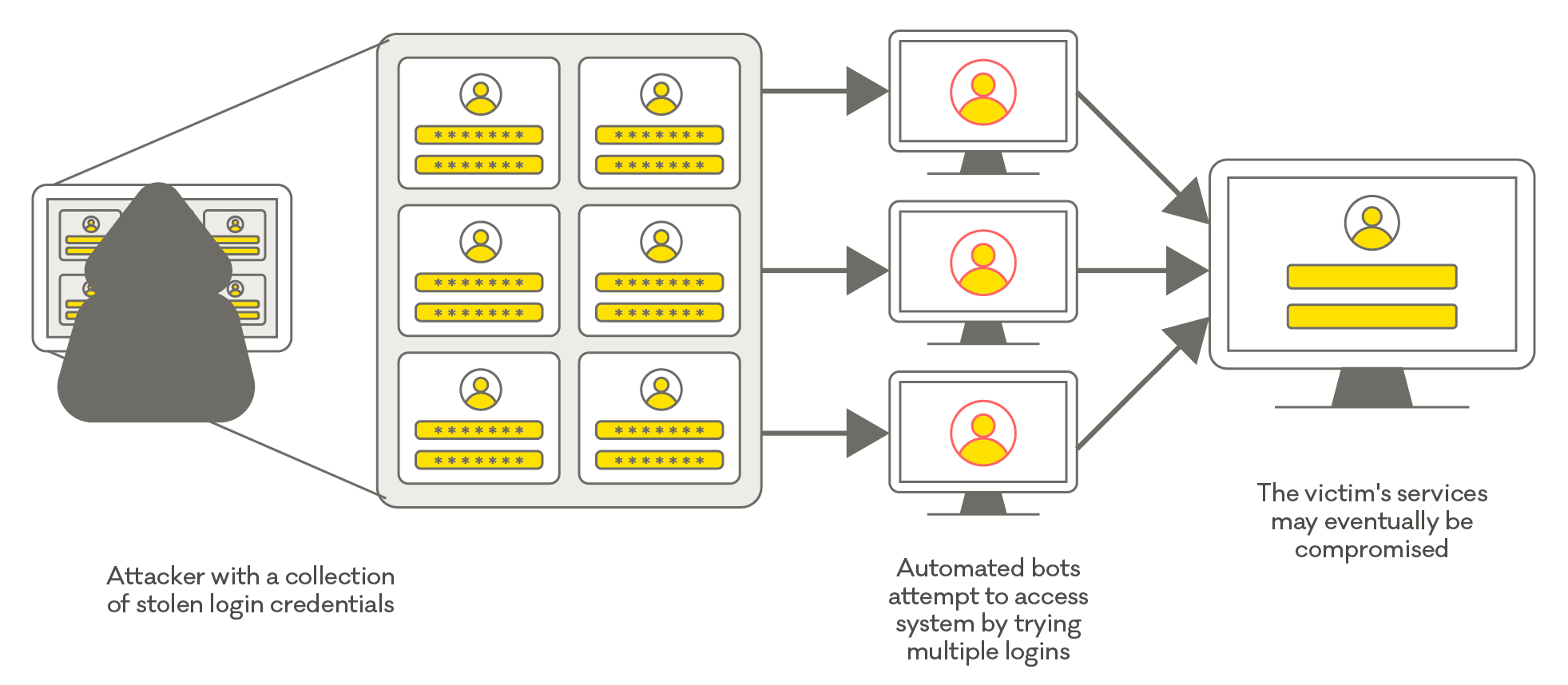
Insight: Insecure computers used for bruteforcing attacks
CERT NZ received 21 reports of bruteforcing from New Zealand IP addresses in Q1 and Q2. Bruteforcing is where attackers try to gain access to systems by trying multiple passwords or passphrases in the hope of eventually landing on the correct one. They usually use automated tools or scripts to do this at a large scale, often using sets of common passwords obtained from data breaches.
Guides to both patching and multi-factor authentication can be found on the CERT NZ website:
Case study: NZTA vehicle license email scam
A sustained phishing campaign by scammers pretending to be the New Zealand Transport Agency (NZTA) has been seen throughout the first half of 2020.
In this campaign, waves of emails were sent to thousands of New Zealanders telling them to renew their vehicle registrations. Taking this action meant the user was directed to a fake NZTA website, from where the attacker could steal their credit card details. Perhaps even more concerning, is that the driver license details obtained by the attacker can be used to commit not only financial fraud, but also identity fraud. Driver license holders may not be aware of this until months or years down the track when they are denied credit.
It’s a good idea to check your credit status every year. That way, you can see if any accounts have been opened in your name.
Instructions on obtaining a free credit report External Link
A further 54 incidents involving phishing sites impersonating well known New Zealand brands were pro-actively identified from our threat intelligence data. This enabled CERT NZ to flag the problem with network operators, website hosting providers and major internet browsers, thereby limiting everyday New Zealanders’ exposure to the attacks.